TPM – a Powerful, Inexpensive Security Building Block
There are two worlds of computer security – high-end systems and then everything else. Both high- and low-end systems typically employ “top-down” defenses to harden their attack surfaces. These are “software-only” security techniques.
High-end and specialized systems have the additional protection of “bottom-up” defenses in the form of Hardware Security Modules (HSMs). HSMs sequester secrets (keys) from the general processing environment ensuring they cannot be stolen if the system is attacked. HSMs for these high-end systems are typically very expensive, making them impractical for low-end systems that still require solid cybersecurity.
How TPMs Can Protect Your Encryption Keys
As cyber-attacks become increasingly more common, there is a need for additional “bottom-up” hardware-based security, including code measurement. Software security measurement systems take a “snapshot” of a system by building transitive trust chains of software measurements (hashes) and storing them in tamper-proof storage. These measurements are used for the following functions:
- Permit “attestation” (cybersecurity health checks) of a system by a remote appraiser.
- “Seal” system secrets preventing their exposure when a system is attacked.
- Authorize security operations based on the real-time health of the system assessed using the measurements.
Comprehensive code measurements are now considered to be a fundamental part of system security. They can be used to detect deep threats (e.g. bootkits and rootkits) which are otherwise undetectable by most “software-only” security solutions (firewalls, anti-virus software, etc.) or by traditional HSMs, which do not have these code measurement capabilities.
How to Use the TPM
A sensible next step in hardware-based security is to combine code measurement with the key protection capabilities of an HSM, resulting in the Trusted Platform Module (TPM) 2.0.
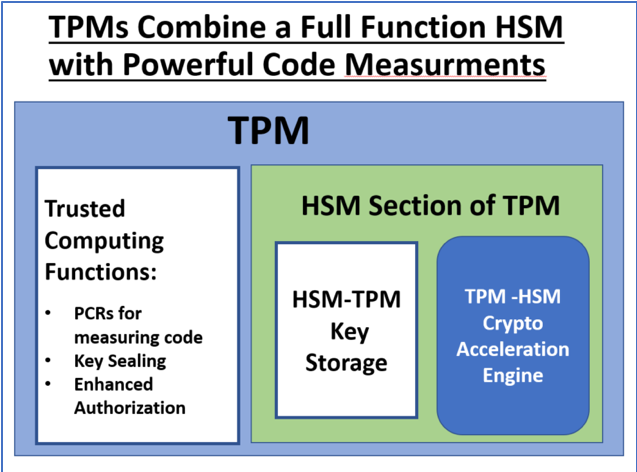
TPM 2.0 meets the performance and low cost requirements of the majority of the world’s computing platforms. TPM 2.0 complies with both Trusted Computing Group and ISO specifications so it is truly an international standard. TPM 2.0 gives all computing platforms – from servers all the way down to the Internet of Things sensors – the robust, modern hardware-based security needed to address the 21st century’s real and ever-growing cybersecurity challenges.
FAQs about TPM Cybersecurity:
What Is a TPM?
TPM stands for Trusted Platform Module, which is a type of hardware security chip that is integrated into computer devices to provide secure storage for encryption keys, digital certificates, and other sensitive information. TPMs are designed to protect against tampering, unauthorized access, and other cyber attacks, making them an important component of modern cybersecurity.
What are the types of Trusted Platform Modules?
There are several types of TPMs available, including discrete TPMs, which are separate chips that are added to a computer’s motherboard, and integrated TPMs, which are built directly into the computer’s processor or chipset. Additionally, there are different versions of TPMs, including TPM 1.2, TPM 2.0, and TPM 2.0 with enhanced capabilities.
What are the main differences between TPM Module vs TPM Platforms?
A TPM module is a discrete hardware component that is added to a computer’s motherboard, while a TPM platform refers to a computer or device that has an integrated TPM chip built into its processor or chipset.
What is a TPM chip?
A TPM chip (Trusted Platform Module chip) is a specialized hardware component that is designed to provide secure storage for sensitive data, such as encryption keys, digital certificates, and passwords. The TPM chip contains a microcontroller and firmware that can perform cryptographic operations, generate and store keys, and authenticate devices, among other functions.
What is the main function of a TPM hardware chip?
TPM chips are typically integrated into computer devices, such as desktops, laptops, and servers, and their main function is to enhance security by protecting against tampering, unauthorized access, and other types of cyber attacks. The use of TPM chips has become increasingly common in modern computing as a way to provide hardware-based security and protect against data breaches and cyber attacks.
 This article was written by Lee Wilson, Business Development Engineer at OnBoard Security since July 2015. Prior to joining OnBoard Security, Lee had a 35 year career with IBM. Initially he did chip design, card design, CAD, and software design.
This article was written by Lee Wilson, Business Development Engineer at OnBoard Security since July 2015. Prior to joining OnBoard Security, Lee had a 35 year career with IBM. Initially he did chip design, card design, CAD, and software design.



