How Adaptive Cyber Security Can Enable Digital Health Adoption
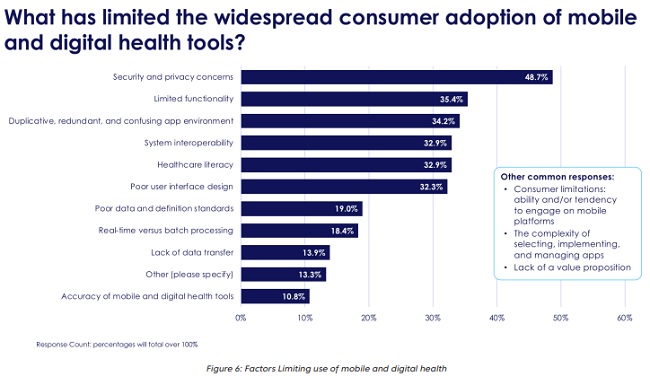
Digital health focuses on connecting the systems, tools, medical devices, and services together that deliver needed healthcare to each of us and gives critical data insights to each player across the healthcare delivery landscape that weren’t available before. According to the recent 8th Annual Industry Pulse Report from Change Healthcare, security and privacy concerns are causing healthcare payers and providers to strongly reconsider whether or not they want to adopt these digital health technologies and mobile tools. In fact, approximately half of all respondents stated that security and privacy were the leading causes of not widely adopting digital health technology, particularly around diagnostic apps and health monitoring devices. Given the amount of coverage recently on healthcare organizations that have experienced a data breach, or been hit with a ransomware attack, this should come as no surprise.
Many healthcare organizations are starting to see cybersecurity as a key driver to support technological innovation that can directly improve patient care. Much of this is being driven by the need to improve and replace much of the outdated IT systems that are currently in place across the overall industry. These systems have shown to be unable to support the interoperability and data processing needs of today’s healthcare market as it shifts to more of a digital platform.
Due to the growth of breaches and attacks in healthcare, many organizations are starting to prioritize cybersecurity as they look to revamp these outdated IT systems. A recent Health IT Security report concluded that 92 percent of healthcare organizations plan to increase their technology spending for cybersecurity needs. What’s interesting, however, is the focus of this spend, based on what many healthcare organizations perceive as the greatest risk.
So much of the security “innovation” over the last decade has focused on faster and more agile identification of threats, viruses and attacks on a network or over a device. The prevailing thought being that the sooner an attack can be identified, the quicker the likely response, resulting in a lessened impact to the business. The underlying problem with this approach is that these tools target identification of threats after an attacker is already on the network or has already taken control of a device. These technologies “detect” rather than “prevent”.
Unfortunately, this causes a great deal of peril to the healthcare industry who is trying to balance the need to implement new digital health technologies to remain competitive with outdated systems and immature security processes. The approach of using these traditional detection tools and products is exacerbating the problem for many healthcare organizations, who are finding that these detection tools simply can’t keep up with the attackers. It’s getting so bad that several healthcare CISOs who were recently surveyed stated that they are so certain they will be subject to a ransomware attack that they are allocating budget to pay the ransom, as this is just easier than dealing with the security issues these products create.
As described earlier, the current mindset on cybersecurity challenges in the healthcare industry caused by these ineffective tools is hindering, even disabling, an organization’s ability to implement digital health technology. However, a different mindset can turn security into an enabler of digital health initiatives, regardless of the state of an organization’s IT infrastructure and processes. How?
The new mindset needs to focus on prevention, rather than detection. We’ve seen that current security technologies simply try to detect the bad actor once they’re in the network. Some security companies are starting to position products that try and prevent the bad actor from accessing the network, but this doesn’t go far enough. The new focus really should be on preventing the bad actor from even seeing or knowing that a network or segment, and the associated applications, systems and devices running on the network, even exist in the first place. Attackers don’t try to breach a network or device that they can’t see or don’t know exists.
This shift is enabled by embedding network cloaking technologies that can significantly prevent the risk of a security breach to their critical patient care delivery systems and connected devices. Cloaking technologies can keep any unknown or unauthorized users from ever seeing these digital health technologies or medical devices, whether they’re legacy or brand-new systems. The risk of a compromise is virtually alleviated when IT systems are visible to only known and authorized identities. Further, cloaking technologies can be implemented prior to a network session being established, so there is no further complexity or management overhead added to a network’s topology.
More about Cybersecurity for Embedded Systems
Adapting one’s security mindset to focus on removing all visibility of a network to unknown or unauthorized actors, even insiders, can allow healthcare organizations to start to receive the potential value of digital health technologies. This new adaptive approach to security can directly enable more effective security capabilities, but also enable greater operational and financial value in supporting digital health initiatives that can improve patient care.
This article was written by Dave Anderson and originally was published on BlackRidge Technology.



