Three Days of Insight into the Rebirth of Michigan – Cybersecurity
Day One
As a proud graduate of The Ohio State University, when I think of Michigan, several things come to mind…but tossing aside for a moment the rivalries of one’s sports-related youth, the images that surface for me tend to be namesakes of a winged variety: The Falcon, The Road Runner, The Firebird. Yes, the sweet sound of street thunder. The muscle cars of a day gone by that earned Detroit the title of Motor City (and to a large extent the entire state of Michigan, the moniker of the automotive mecca of the world or at the very least North America) represent a time of pride and abundance for the heartland of America.
As my Uber driver slid past a Grand AM on the way to the airport, it struck me that the one bird that I truly longed to see emerge from that State to my Northwest wasn’t one of the namesakes I mentioned earlier, but definitively one of a burning nature. Pondering this thought, I thanked Lawrence my driver for the ride and headed into CLE bound for a three-day press tour of Michigan’s state-wide Cybersecurity initiative.
Day Two
Our first stop of the day was an introductory breakfast at The Apparatus Room, (I highly recommend the Foundation Breakfast Sandwich – fried egg, arugula, black garlic aïoli, house-made rashers, all on a toasted English muffin, which is accompanied by a handsome portion of roasted potatoes). Here I met my cohorts in crime; Byron Acohido, Wes O’Donnell, and Robert Katz, along with the team from the Michigan Economic Development Company who were hosting us. Following breakfast, we headed over to the newly remodeled COBO Center for the 2018 North American International Cyber Summit.
The Summit, hosted by Rick Snyder, Michigan State Governor, and a self-proclaimed nerd, was well attended (total number of attendees 876) with representation from AZ, CT, IL, MA, MD, MI, MN, OH, TX, WA, VA, Canada, and Africa. Multiple sessions on topics ranging from mitigation techniques for Car Hacking to preventing attacks on cyber-physical fronts were available for attendees.
 The final round of competition for the 3rd Annual Governor’s High School Cyber Challenge, an event that tests high school students from across the state in the areas of computer science, information technology, and cybersecurity via a two-round statewide competition, also took place during the Summit. October 1-4, 223 teams comprised of 650 students competed in round one of the Challenge with 10 teams advancing to the finals. Congratulation to this year’s winners: 1st Place: Cadillac High School – Cyber Vikings; 2nd Place: Marquette Senior High School – Team MSHSl; 3rd Place: Okemos High School – Chiefs.
The final round of competition for the 3rd Annual Governor’s High School Cyber Challenge, an event that tests high school students from across the state in the areas of computer science, information technology, and cybersecurity via a two-round statewide competition, also took place during the Summit. October 1-4, 223 teams comprised of 650 students competed in round one of the Challenge with 10 teams advancing to the finals. Congratulation to this year’s winners: 1st Place: Cadillac High School – Cyber Vikings; 2nd Place: Marquette Senior High School – Team MSHSl; 3rd Place: Okemos High School – Chiefs.
A virtual trip to Alphaville was also available for those looking to test their technical prowess at hacking an entire city real time via The International Cyber Exercise, an annual multi-team event that allows participants to face off in a real-time battle to control as many of Alphaville’s assets as possible. Alphaville, a virtual training realm created by the Michigan Cyber Range, can accommodate 30 independent teams simultaneously who must vie both offensively and defensively to gain control over as much of the city as possible. The system can accommodate 30 different scenarios of competition from force on force, static, to capture the flag. The team controlling the most assets at the end of 24 hours wins. The Exercise is one of the world’s largest non-classified events of this type.
The range incorporates a bank, private energy company, electric grid, school system, and several other virtual commercial entities. An event unto itself, the Alphaville hack was attempted by participants from Maryland, Minnesota, Michigan, New Hampshire, New Jersey, and Wisconsin all of whom competed against the Michigan Army National Guard team. As the name implies though the event is not limited to a national scope as eleven other Nation States (Albania, Croatia, Estonia, Georgia, Latvia, Portugal, and Serbia as well as four others) entered the competition this year as well to test their abilities against the best of the best.
Major General Gregory J. Vadnais from the Michigan National Guard took a break from the competition to explain some of the initiatives in which they are engaged. Vadnais stated that engagement is a great example of collaboration between NATO counties  and an outstanding opportunity for knowledge sharing. When asked how these nations are identified to engage in the competition. Major General Vadnais said that because of the relationships that the National Guard teams maintain with their foreign counterparts, a simple phone call is sometimes all that is necessary to pull a nation-state into the competition. The team at Merit collaborates with the Cyber Command to initiate the dialog. To date, international participation has mainly been focused on Europe. Major General Vadnais noted that the UK Army has participated in the past and the only country participating this year that is not involved in the State Partnership program is Portugal. The team from Merit jokingly commented that the defense attaché from Portugal called and asked, “Hey can we play.” so he contacted the TAG office and got authorization for them to engage too.
and an outstanding opportunity for knowledge sharing. When asked how these nations are identified to engage in the competition. Major General Vadnais said that because of the relationships that the National Guard teams maintain with their foreign counterparts, a simple phone call is sometimes all that is necessary to pull a nation-state into the competition. The team at Merit collaborates with the Cyber Command to initiate the dialog. To date, international participation has mainly been focused on Europe. Major General Vadnais noted that the UK Army has participated in the past and the only country participating this year that is not involved in the State Partnership program is Portugal. The team from Merit jokingly commented that the defense attaché from Portugal called and asked, “Hey can we play.” so he contacted the TAG office and got authorization for them to engage too.
Major General Vadnais further highlighted that The Michigan National Guard maintains the largest reserve component training site in the nation. With 147,000 acres and as large an air space pocket as Nellis Air Force Base in Las Vegas Valley, NZ, Camp Grayling can offer all five domains of warfare: Air, Sea, Land, Space, and Cyber. Griffinville, as described below, is an integration of Camp Grayling into the Cyber realm. This is enabled under the classification of Defense support to civil security; however, it was pointed out by Merit representatives that they need to maintain the project at an unclassified level.
TARDAC’s Combined Arms Training Facility, which incorporates 26 buildings represents an entire city that is all wired to capture the sites and sounds of a battlefield. Videography is now tied with cyber capabilities to incorporate them real-time into the event. The Army National Guard also maintains control of the spectrum at the base. This was granted by the FCC, so that the camp can perform truly realistic drills. A simulation referenced from earlier this year illustrated how a team was able to hack the operation network and “fuzz” the GPS systems of a training operation. Major General Vadnais emphasized that this type of an attack; manipulation vs. disablement, is where real implications lie so it is critical to understand these types of tactics and be able to defend against this type of attack.
As a final point, Major General Vadnais commented that “We tend to think in a kinetic way but Cyber, is the new domain of warfare.”
 In addition to a purely virtual throwdown, for those looking for a bridge between the virtual and real world, a trip to Griffinville is an option as well. Griffinville is a virtual twin of the Combined Army Combat Training Facility (CACTF) located at Camp Grayling, MI that is accurate to the inch. The simulation offers cyber teams a virtual engagement with the infrastructure and systems to assist or circumvent the maneuvers currently underway at the Camp, virtually speaking of course. “Griffinville represents…the first step between building the bridge between cyber and kinetic domains of warfare for commanders and soldiers of the future”.
In addition to a purely virtual throwdown, for those looking for a bridge between the virtual and real world, a trip to Griffinville is an option as well. Griffinville is a virtual twin of the Combined Army Combat Training Facility (CACTF) located at Camp Grayling, MI that is accurate to the inch. The simulation offers cyber teams a virtual engagement with the infrastructure and systems to assist or circumvent the maneuvers currently underway at the Camp, virtually speaking of course. “Griffinville represents…the first step between building the bridge between cyber and kinetic domains of warfare for commanders and soldiers of the future”.
Kibbey the Cyber Dog, a proud employee of the Michigan State Police Department, was also in attendance with her handler, Michigan State Trooper, David Cardenas. In the same way other service dogs can locate explosives or drugs, Kibbey is able to detect and locate items ranging in size from a flash drive or micro SD card to a laptop by homing in the scent of a specific chemical, Triphenylphosphine, that is used in the conformal coating of printed circuit boards (PCB boards) within electronic devices.
Officer Cardenas and Kibbey are brought in on computer crimes cases as the secondary  search for locations. Prior to Kibbey coming on the scene, the primary search teams will remove as many of the decoys from the area as possible such as remote controls, electronic device chargers, cellular phones that may or may not be deemed as evidence so that Kibbey’s keen olfactory skills can be leveraged to locate potentially hidden devices that perpetrators were intending to keep from being found. Cardenas stated that “Just this morning [we] found a flash drive and cell phone stashed in the basement rafters and a couple hard drives in totes that were in storage.” On a lighter note, Cardenas laughed that he and his kids never have to worry about losing their TV remote control any longer, as a simply “Kibbey go find it,” is all it takes to locate the missing device.
search for locations. Prior to Kibbey coming on the scene, the primary search teams will remove as many of the decoys from the area as possible such as remote controls, electronic device chargers, cellular phones that may or may not be deemed as evidence so that Kibbey’s keen olfactory skills can be leveraged to locate potentially hidden devices that perpetrators were intending to keep from being found. Cardenas stated that “Just this morning [we] found a flash drive and cell phone stashed in the basement rafters and a couple hard drives in totes that were in storage.” On a lighter note, Cardenas laughed that he and his kids never have to worry about losing their TV remote control any longer, as a simply “Kibbey go find it,” is all it takes to locate the missing device.
We also had the opportunity to meet with Jim Ellis, who leads the Cyber program for the Michigan State Police. An example of collaboration and partnership between state departments is another area where Governor Snyder took action during his terms. In 2011/12 he stood up the Michigan Cyber Command Center, which was inserted into the Computer Crimes unit’s cyber section, the MC3 under the State Police Department. The DTMB, National Guard, and federal partners such as the FBI Cyber Task Force along with the Michigan State Police (MSP) collaborate on Cyber Crime and are all housed in a joint Lansing Base of operations. Six offices throughout MI are engaged in Cyber or Computer Crime. Key sectors of focus and collaboration noted by Ellis were energy, healthcare, and finance.
The Center offers local government support for SME organizations that lack internal IT or do not have ties to a federal agency. Ellis pointed out that the key is to call before you need them. When asked to describe the landscape in the area of ransomware, Ellis commented, “attempts are getting more sophisticated. They see a few variants that can be decrypted without paying a ransom, but very few.” Prevention and awareness are critical as well as backups and disaster recovery plans. When asked how much of the department’s time is dedicated on the proactive side, Ellis stated that their department was engaged in 300 outreach opportunities last year. He has a full-time position allocated for outreach. To frame the level of growth in this area Ellis stated that the Michigan Cyber command center was at 9 people 5 years ago. Today they number 56 and he is asking for another 20 heads by 2020, which would start October 1, 2019. When asked how Michigan’s program compares to other states, Ellis stated that through the NGA resource center for cross-state collaboration he has visited numerous states to aid in various capacities.
 By his estimation, Michigan is in the top 5 throughout the US in terms of their general cyber posture and how they collaborate. As day one of the tour marched on, it became apparent that the coordinated progress that was demonstrated across Michigan was not a chance occurrence but was, in fact, the result of a well-orchestrated plan over ten years in the making. The catalyzing vision behind Michigan’s Cyber initiative was confirmed when I had the opportunity to sit down with Governor Snyder and David Devries, Director and State of Michigan CIO in Michigan. Governor Snyder credits his experience with Gateway, Inc. (Remember the “other” direct sell PC company of the 90s that enshrined their technology in Holstein embroidered boxes), as well as Avalon Investments Inc. and Ardesta LLC., the two Venture Capital companies he co-founded following his exit from Gateway Inc., as giving him the insight to not only identify Cyber Security as a critical area of focus but to put a plan together to take State level action over his two terms in office. Snyder went on to say that at the NGA (National Governors Association) when the topic of Cybersecurity was tabled for discussion and collaboration, he could not get some of the governors to show up because they didn’t think it was an issue.
By his estimation, Michigan is in the top 5 throughout the US in terms of their general cyber posture and how they collaborate. As day one of the tour marched on, it became apparent that the coordinated progress that was demonstrated across Michigan was not a chance occurrence but was, in fact, the result of a well-orchestrated plan over ten years in the making. The catalyzing vision behind Michigan’s Cyber initiative was confirmed when I had the opportunity to sit down with Governor Snyder and David Devries, Director and State of Michigan CIO in Michigan. Governor Snyder credits his experience with Gateway, Inc. (Remember the “other” direct sell PC company of the 90s that enshrined their technology in Holstein embroidered boxes), as well as Avalon Investments Inc. and Ardesta LLC., the two Venture Capital companies he co-founded following his exit from Gateway Inc., as giving him the insight to not only identify Cyber Security as a critical area of focus but to put a plan together to take State level action over his two terms in office. Snyder went on to say that at the NGA (National Governors Association) when the topic of Cybersecurity was tabled for discussion and collaboration, he could not get some of the governors to show up because they didn’t think it was an issue.
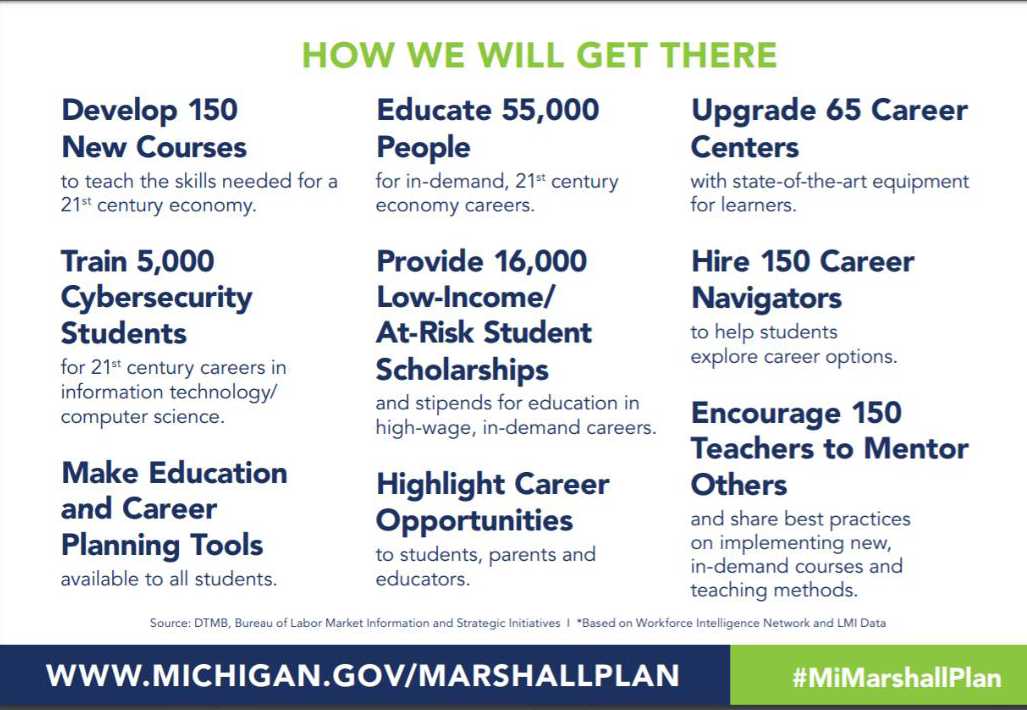 The culmination of this vision was the creation of The Marshall Plan for Talent. The plan recognizes that the educational system needs to be transformed to align with the jobs of tomorrow. An “Investment in Talent”, the plan seeks to fill the gap between what industry needs and what academia is currently positioned to produce. Michigan is allocating $100,000,000 over the next five years toward this endeavor. There are over 800,000 jobs forthcoming by the year 2024 in the state of Michigan alone that will require new skill sets. The plan looks to create multiple connections to business, to prepare the students of today (K-12, to Vocational, to University, as well as redeployment of today’s displaced workforce) for the opportunities of tomorrow. The plan’s foundation is anchored on a strategy of four pillars: Increase Career Exploration; Evolve to Competency Based Learning; Foster Business and Education Collaboration; and Create Multiple Pathways. In support of the strategy, the State has developed 9 key measurable tactics to leverage as follows: A critical success factor to this integration, alignment, and connection is the underlying connectivity required to enable it. Dashboard metrics for everything they are doing are critical to success as Governor Snyder stressed this fact and made the comment, “How do you know if you’re succeeding if you don’t measure it?”
The culmination of this vision was the creation of The Marshall Plan for Talent. The plan recognizes that the educational system needs to be transformed to align with the jobs of tomorrow. An “Investment in Talent”, the plan seeks to fill the gap between what industry needs and what academia is currently positioned to produce. Michigan is allocating $100,000,000 over the next five years toward this endeavor. There are over 800,000 jobs forthcoming by the year 2024 in the state of Michigan alone that will require new skill sets. The plan looks to create multiple connections to business, to prepare the students of today (K-12, to Vocational, to University, as well as redeployment of today’s displaced workforce) for the opportunities of tomorrow. The plan’s foundation is anchored on a strategy of four pillars: Increase Career Exploration; Evolve to Competency Based Learning; Foster Business and Education Collaboration; and Create Multiple Pathways. In support of the strategy, the State has developed 9 key measurable tactics to leverage as follows: A critical success factor to this integration, alignment, and connection is the underlying connectivity required to enable it. Dashboard metrics for everything they are doing are critical to success as Governor Snyder stressed this fact and made the comment, “How do you know if you’re succeeding if you don’t measure it?”
To peel back the onion a bit further on how the state plans to allocate the $100 million, I was able to speak with Jeremy Hendges, Chief Deputy Director, and Dan Olsen, Communications and Media Relations Manager with the State of Michigan Talent and Economic Development (TED) Department. Olsen explained that the State has assigned $59 million to be awarded for Innovation Grants that are allocated across four different buckets:
- Nearly $28 million in support for new and expanded world-class curricula. This would be used to create open-source curriculum, materials, professional development and lesson plans that follow competency-based principles for programs that do not exist or fill gaps in existing programs for high-demand, high-wage careers in Michigan.
- $18.5 million in professional equipment grants for state-of-the-art equipment that support new or existing programs for high-demand, high-wage careers. A 25 percent match is required.
- $2 million to help support schools converting to a competency-based instruction model.
- $10.5 for career navigators/career counselors – folks who can help students explore available career pathways and develop meaningful learning plans.
A complement to this is the Choose Michigan campaign designed to attract and retain talent to the state. Taking even a high level review of the material yields some pretty compelling reasons for an individual or organization to consider Michigan and this is coming from a Buckeye: 4th most affordable state in the union (a great thought unless your just dying to allocate the entirety of your lottery winnings toward the down payment on a house in Palo Alto, “just sayin”); more engineers live in Michigan than any other state; #3 in Tech Job growth nationally; and 9/10 of the largest aerospace/defense R&D firms have a footprint in Michigan; just to name a few.
As for the remaining $41 million, $4 million is marked for integrated teacher core development and deployment to give educators who have developed bleeding edge programs and content the ability to replicate their core across the state. $25.5 million is assigned for Talent for Tomorrow scholarships, stipends, and grants. A program designed to provide support services for individuals seeking education in high demand / high wage fields as well as support for wraparound services that will provide low income and unemployed individuals redeployment opportunities. The balance of $7.5 million is for talent promotion, retention, and attraction initiatives. Three of the cities being targeted are Boston, MA; Madison, WI; and Chicago, IL. A portion of the $7.5 million is assigned for the Expanding MI Bright Future campaign, which is a career exploration tool for students.
To better understand the networking piece of the puzzle we sat down Joe Adams, inventor of the Cyber Range and VP of Research and Development at Merit, for insight 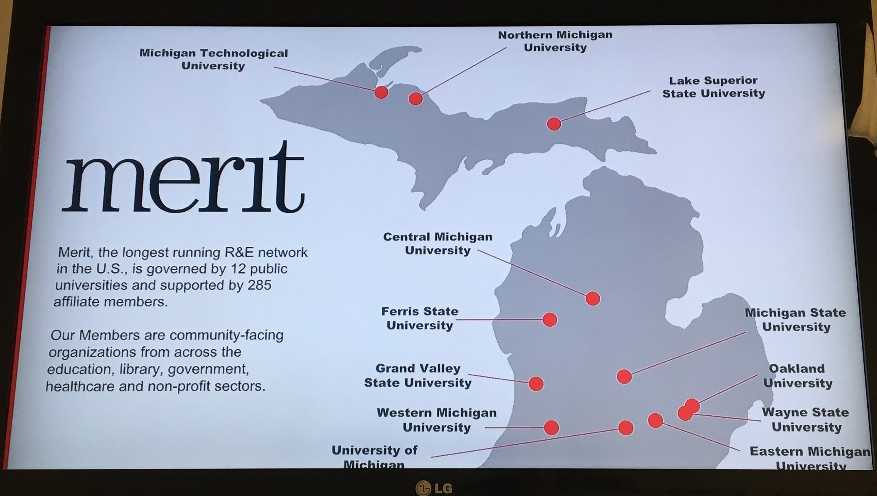 into the backbone of Michigan’s connectivity and the Cyber Range. Merit Network’s infrastructure is Michigan’s research and education network. It is comprised of approximately 4000 miles of a fiberoptic network through the state and a private cloud that contains the range. Users encompass everyone one from high schools to professionals. There is only one range, and currently, there are eight physical HUBs from which the Range can be accessed. Merit connects all 555 high schools in the state, all the 4-year colleges, 86% of the two-year colleges, as well as most of the libraries. Merit is partnered with the state in this initiative. The state identifies locations within communities to house a HUB site that gives a physical location for access. They teach individual certifications for high school students, returning veterans, chronically unemployed folks, and offer job retraining. Fundamentals of IT, security plus (a blue team defensive approach). Adams commented that “[Michigan’s Research and Education network] is one arm of Merit’s business representing approximately 20%. The other 80% is internet connectivity. Network security for any not-for-profit community-based organization that is a member of Merit. Merit is a nonprofit incorporated in 1966. We literally helped build the internet and were on the NSF net, NCI net.” Merit is deeply rooted in education. They provide connectivity to K12, the library network, blood banks, and museums.
into the backbone of Michigan’s connectivity and the Cyber Range. Merit Network’s infrastructure is Michigan’s research and education network. It is comprised of approximately 4000 miles of a fiberoptic network through the state and a private cloud that contains the range. Users encompass everyone one from high schools to professionals. There is only one range, and currently, there are eight physical HUBs from which the Range can be accessed. Merit connects all 555 high schools in the state, all the 4-year colleges, 86% of the two-year colleges, as well as most of the libraries. Merit is partnered with the state in this initiative. The state identifies locations within communities to house a HUB site that gives a physical location for access. They teach individual certifications for high school students, returning veterans, chronically unemployed folks, and offer job retraining. Fundamentals of IT, security plus (a blue team defensive approach). Adams commented that “[Michigan’s Research and Education network] is one arm of Merit’s business representing approximately 20%. The other 80% is internet connectivity. Network security for any not-for-profit community-based organization that is a member of Merit. Merit is a nonprofit incorporated in 1966. We literally helped build the internet and were on the NSF net, NCI net.” Merit is deeply rooted in education. They provide connectivity to K12, the library network, blood banks, and museums.
Following the meeting with Merit, we had a short session with Fritz Erickson, President; Gavin Leach, VP Finance & Administration; Dr. Steve VandenAvond, VP Extended Learning Community Engagement; and Dave Nyberg, Director corporate engagement at Northern Michigan University. Northern was one of the first universities back in the 90s to give every student a laptop. Soon following was the realization that WIFI access would be a necessity as well. So, they created a model that gave access to everyone within a 25-mile radius of the Northern campus. Fritz jokingly stated that “for a community that has more deer than people that’s a pretty remarkable thing.” The next phase of the plan will be insuring WIFI access from anywhere across a 21,000 mi2 area of the upper peninsula (UP). So, Northern Michigan University has a long-standing position of supporting technology in a rural environment. They maintain an LT system running throughout the UP now. The university functions as a technology HUB for the UP, providing a connection for students as well as the communities in the northernmost region of the State.
 Midafternoon we departed the Conference for a visit with Duo Security in Ann Arbor for a chat with Co-Founder, Chairman & CEO Dug Song. Duo’s global headquarter was the original home of the Ann Arbor Organ Company (noted by the dedicated instrument in the lobby pictured here). Duo’s mission is to democratize security. Dug explained, “Our goal is to make security something every organization can achieve without all the headache, cost, and potentially all the people, as have been required in the past.” Security and usability are generally two things that are perceived as being mutually exclusive, one is about saying no, the other is about saying yes. Design engineering is about making sure only the right things happen by designing to the needs and expectations of their users. So, at Duo, they focus on making security that stays out of your way, is understandable, and still providing value. Selling a negative is always a difficult task so Duo focuses on making sure the right thing to do the easiest thing to do.
Midafternoon we departed the Conference for a visit with Duo Security in Ann Arbor for a chat with Co-Founder, Chairman & CEO Dug Song. Duo’s global headquarter was the original home of the Ann Arbor Organ Company (noted by the dedicated instrument in the lobby pictured here). Duo’s mission is to democratize security. Dug explained, “Our goal is to make security something every organization can achieve without all the headache, cost, and potentially all the people, as have been required in the past.” Security and usability are generally two things that are perceived as being mutually exclusive, one is about saying no, the other is about saying yes. Design engineering is about making sure only the right things happen by designing to the needs and expectations of their users. So, at Duo, they focus on making security that stays out of your way, is understandable, and still providing value. Selling a negative is always a difficult task so Duo focuses on making sure the right thing to do the easiest thing to do.
 Dug went on to demonstrate the attributes and advantages of their product such as the single sign-on (SSO) that enables all the applications on the network as well as those that are running in the cloud to once again make the easiest path the safe path. He pointed out that what transpired in that split second between log on attempt and authorization being granted was a full remote interrogation of the security posture of the device being used to log in. This is made possible through multiple partnerships that Duo has in place with players such as Google and Microsoft, which enable APIs to be leveraged to verify if the device has been tampered with since the last successful login; a concept referred to as Remote Attestation. At a high level, the device simply becomes a portal to access all the software and operations running in the cloud.
Dug went on to demonstrate the attributes and advantages of their product such as the single sign-on (SSO) that enables all the applications on the network as well as those that are running in the cloud to once again make the easiest path the safe path. He pointed out that what transpired in that split second between log on attempt and authorization being granted was a full remote interrogation of the security posture of the device being used to log in. This is made possible through multiple partnerships that Duo has in place with players such as Google and Microsoft, which enable APIs to be leveraged to verify if the device has been tampered with since the last successful login; a concept referred to as Remote Attestation. At a high level, the device simply becomes a portal to access all the software and operations running in the cloud.
Duo also has a free tool called Duo Insight that is a phishing tool that helps you assess how susceptible your organization is to attack. The tool essentially tells you how easily passwords can be phished from your organization. As a significant portion of Duo client base is Academia (from Big Ten to Ivey League), Dug shared an example from one university where many students descended upon the registrar’s office to find out why they had been dropped from a course. The records indicated that all the students had logged in and dropped the course. Digging a little deeper, they realized that all the students’ direct deposit accounts had been redirected to a bank in Eastern Europe and all the corresponding refunds for the course cancelations were being redirected there. The volume of potential students makes universities a prime target for this type of attack coupled with the reality that parents will most likely not detect the situation for some time. “You can harden your networks, but people will always be sort of soft and squishy and so they make very good targets into people’s organizations…how do we make security that will defend the new perimeter, the user?” Dug rhetorically offered.
Dug went on to explain why he chose Michigan to be home base for Duo. He met his wife in Ann Arbor, a city that is continually a top contender for the most educated city in America and home to many of the individuals that built the internet. A city within a state that imports brains and ship them out, the people of Ann Arbor tend to be very open-minded about collaboration and education.
To exemplify this spirit of collaboration and support, Dug introduced us to Brian Kelly, Founder & CEO; and Sally Feller, PR & Marketing Manager from censys. Brian left Duo to create censys, a startup offering insight into the backbone of the internet i.e. real-time search capability for all devices that are connected to the internet globally, yes globally. Like a Google search for content, censys offers search capability to identify servers, routers or any device that has a service on it that is connected to the internet. A 13 person startup with recently secured funding in place, and 60 paying customers, censys appears to be riding the entrepreneurial wave of success. Dug is now a board member of censys.
From Duo, our tour proceeded to a networking reception at PlanetM Landing Zone where we were afforded the opportunity to learn more about this partnership between the Detroit Regional Chamber and the Michigan Economic Development Corp. (MEDC) and speak with some of the other folks whom we met earlier that day at the Cyber Conference.
 A short tour by Kathryn Snorrason, Business Development Manager at Planet M, offered a glimpse into the mission of the Landing Zone, which simply put is to make it as easy as possible for the world’s best mobility companies to bring their innovation to market in North America.
A short tour by Kathryn Snorrason, Business Development Manager at Planet M, offered a glimpse into the mission of the Landing Zone, which simply put is to make it as easy as possible for the world’s best mobility companies to bring their innovation to market in North America.
The PlanetM Landing Zone offers access to a State subsidized collaborative workspace for mobility focused startups that provides the opportunity to rub elbows with other industry players, potential partners, decision-makers and other like-minded organizations while at the same time providing access to facilitators and connectors from the MEDC’s network and resources. At a rate of $100/desk per month for the first six months and $200/desk per month thereafter with access to private offices (on a first come/first serve basis), the Landing zone provides an ideal incubator environment.
Following the mixer, we were off to TownHouse Detroit for dinner, a little decompression from an immensely full day, and a brief tee up for the following day’s activities.
Tuesday, October 30 promised insight into several other Michigan startups as well as tours of Pinkney Cyber Training Facility and WMCAT (Western Michigan Center for Arts and Technology), two of the Cyber HUB training facilities that make up the evolving connected network of Michigan’s Cyber Range.
Day Three
The crack of dawn brought our team to, yet another foodie’s 
 dream come true, with a brief stop for breakfast at to the Detroit Institute of Bagels. My TBA signature sandwich (Turkey, bacon, avocado, gouda, lettuce, tomato & spicy mayo) on an everything bagel, accompanied by a much-needed cup of and dark roast, catalyzed my day into high gear day. Score one more for Motor City. So, with our stomachs full and a robust agenda ahead of us, we headed out for all points Grand Rapids; first stop, Pinckney Cyber Training Institute.
dream come true, with a brief stop for breakfast at to the Detroit Institute of Bagels. My TBA signature sandwich (Turkey, bacon, avocado, gouda, lettuce, tomato & spicy mayo) on an everything bagel, accompanied by a much-needed cup of and dark roast, catalyzed my day into high gear day. Score one more for Motor City. So, with our stomachs full and a robust agenda ahead of us, we headed out for all points Grand Rapids; first stop, Pinckney Cyber Training Institute.
 The Pinckney Cyber Training Institute, located within the Pinckney Community High School, was designed specifically to support 21st-century approaches to learning. According to Dr. James Darga, Director of the Pinckney Cyber Training Institute and Sentinel Center, “[the Institute] is an educational institute that provides a cybersecurity experience for students, civilian adults, and military professionals statewide.”
The Pinckney Cyber Training Institute, located within the Pinckney Community High School, was designed specifically to support 21st-century approaches to learning. According to Dr. James Darga, Director of the Pinckney Cyber Training Institute and Sentinel Center, “[the Institute] is an educational institute that provides a cybersecurity experience for students, civilian adults, and military professionals statewide.”
The high school program has been the core of the center. Based on the Cisco Networking Academy curriculum, Computer networking and cybersecurity pathways are both leveraged in the program. The curriculum is also supplemented with content from Comtia (Computing Technology Industry Association) network + and security +. For the adult educational portion, the center offers a Cybersecurity Analysist certification and a Cyber Security Vulnerability Assessor / Ethical Hacker Certification.
 The center services five high school districts within the region in addition to the student body at Pinckney Community High School. Students can drive or busing is available. Pinckney county does not have a career center per se. Their approach to this is to incorporate specialty areas into each of the schools. Cyber Security, Computer Networking, Robotics Automotive Technology, Manufacturing and Welding. As they do not have a community college within the county, Pinckney formed a partnership with Washtenaw Community College, to create an early
The center services five high school districts within the region in addition to the student body at Pinckney Community High School. Students can drive or busing is available. Pinckney county does not have a career center per se. Their approach to this is to incorporate specialty areas into each of the schools. Cyber Security, Computer Networking, Robotics Automotive Technology, Manufacturing and Welding. As they do not have a community college within the county, Pinckney formed a partnership with Washtenaw Community College, to create an early  middle college for post-secondary educational opportunities.
middle college for post-secondary educational opportunities.
Emersion is a key aspect of the approach. A great deal of focus is made at Pinckney to give real-world exposure to the students across programs. It is this interdisciplinary approach and opportunity for learning that resonated to me.
 Departing Pinkney, we headed to Wolfgang Puck’s The Kitchen located in the Amway Grand Plaza Hotel for a networking lunch with some of the western side of the state’s innovators and Entrepreneurs in the Cyber Space.
Departing Pinkney, we headed to Wolfgang Puck’s The Kitchen located in the Amway Grand Plaza Hotel for a networking lunch with some of the western side of the state’s innovators and Entrepreneurs in the Cyber Space.
Much like a round of speed dating, we enjoyed some exquisite cuisine while rotating through a series of fast-paced conversations with representatives from GRIMM, VDA Labs, Presidio, US Signal, Jadex Dornerworks, and a supportive and most hospitable contingent from The Right Place (Western Michigan’s leading economic Development Organization), as well as our escorts, form the MEDC and Weber Shandwick.
Following lunch, we were on our way to the WMCAT Cyber HUB gain insight into how this node on the cyber range fit into the puzzle.
 WMCAT is a nationally-recognized leader in creative youth and adult workforce development. An action-oriented organization that tenaciously focuses on equity, WMCAT by their own admission “curate[s] a place where teens and adults can elevate their voices and leverage their lived experiences to choose their own unique opportunity pathways.”
WMCAT is a nationally-recognized leader in creative youth and adult workforce development. An action-oriented organization that tenaciously focuses on equity, WMCAT by their own admission “curate[s] a place where teens and adults can elevate their voices and leverage their lived experiences to choose their own unique opportunity pathways.”
Workforce Development offers under and unemployed men and women the opportunity to learn a new career, grow personally and professionally, and build a network with industry and community leaders.”
We had the opportunity to meet with Anthony Tuttle, Manager, Cyber & IT Initiatives at WMCAT to tour their new facility (pictured above) and learn firsthand about their programs and approach to community engagement. Anthony role is to lead WMCAT’s charge in building a diverse and inclusive cybersecurity and technology talent pipeline in West Michigan and ultimately maximizing the community’s utilization of the region’s only neutrally-located, community-based Cyber Hub for workforce development in the IT and cybersecurity sectors.
We were greeted by the onslaught of high school students who just arriving for their afternoon sessions as we departed WMCAT for the last destination on our tour, GRIMM, to see their new Cyber Security Testing facility in Sparta, Michigan.

GRIMM is a cybersecurity, engineering, and consulting firm that specializes in helping both government and commercial organizations assess, refine and resolve their current situation as it relates to cybersecurity. GRIMM serves the Transportation sector, IOT Space, Federal Defense and Intelligence, Critical Infrastructure, Banking Finance and Digital Currencies, and Medical IT & Healthcare spaces. Brian Demuth, GRIMM’s CEO came on board roughly two years ago. During a one on one interview with Brian, he stated that they settled on Sparta mainly because several of their employees were from the area and did not want to relocate. Additionally, Sparta’s regional airport offers easy access for GRIMM’s Aerospace clients to bring projects to their doorstep. Similarly, they are close enough to the big three to offer ease of access to their automotive clients. Brian commented that proximity to the auto sector makes it that much less work for the car companies to get their skunkworks vehicles to their facility for testing without the spies or inquisitive eyes of Car & Driver, Road, and Track, or Motor Trend being able to sneak a peek.
The team at GRIMM is currently in the process of remodeling their new facility. Preliminary work has begun already but the team has big plans for expansion in the coming months to flesh out the new facility footprint and optimize the space to meet their clients’ testing needs.
 The former site of Cellar Brewing, space offers the room and layout GRIMM was seeking. In addition to general remodeling, the team has plans to add on a 30’ x 40’ two-story tall addition to the front of the building. The end state of GRIMMS new home will be a combination of an advanced cyber research facility and mechanics shop with a lift big enough to accommodate large trucks as well as tanks and possibly an occasional helicopter. As one can imagine they will be adding quite a bit of security systems as well due to the nature of their work and clients.
The former site of Cellar Brewing, space offers the room and layout GRIMM was seeking. In addition to general remodeling, the team has plans to add on a 30’ x 40’ two-story tall addition to the front of the building. The end state of GRIMMS new home will be a combination of an advanced cyber research facility and mechanics shop with a lift big enough to accommodate large trucks as well as tanks and possibly an occasional helicopter. As one can imagine they will be adding quite a bit of security systems as well due to the nature of their work and clients.
Howdy Neighbor, the dollhouse incorporating dozens of hackable IOT devices, offers a challenge to hacking each one of them and 3PO, the mobile vehicle hacking lab, both pictured above, are just two examples of hands-on ways that GRIMM engages with the community to help stimulate, educate, build awareness, and interest in the growing world of cybersecurity. GRIMM is also the creators of the ICS Village, a non-profit arm of the business that seeks to enlighten and aid industry and policymakers in how to defend the Industrial Control System (ICS) space from threats through hands-on engagement.
After thoroughly enjoying the tour, demonstrations, and conversation with the GRIMM team, we thanked Brian and the team at GRIMM for the hospitality and for sharing their new test lab with us and headed to Terra to experience one of Grand Rapids shining stars in the culinary scene.

 Terra succeeded in achieving the goals of their mission statement, “[To offer] Inspired, handcrafted foods that nurture both body and community. At Terra, we follow our passions – and the seasons – for only the freshest, health-filled ingredients from the region’s most dedicated growers.” The Caesar Salad with sarvecchio & anchovies and Autumn Bisque with Shrimp were a wonderful way to capstone the day. The chai coconut cream, apple onion jam and essence of sesame caught the spirit of the season and trip quite remarkably.
Terra succeeded in achieving the goals of their mission statement, “[To offer] Inspired, handcrafted foods that nurture both body and community. At Terra, we follow our passions – and the seasons – for only the freshest, health-filled ingredients from the region’s most dedicated growers.” The Caesar Salad with sarvecchio & anchovies and Autumn Bisque with Shrimp were a wonderful way to capstone the day. The chai coconut cream, apple onion jam and essence of sesame caught the spirit of the season and trip quite remarkably.
Halloween morning came early as I needed to get back in time to prepare for the trick or treaters that were preparing to descend upon communities everywhere in search of a bounty of sugar and chocolate filled delights to tide them over until the holiday season is fully at hand. So, as I sipped my dark roast at the Airport Starbucks and reflected on all that I had seen over the past three days, I pondered the question that I had asked myself before I left: Will the Cybersecurity industry be the catalyst to help Michigan rise again like a phoenix from the ashes? Based on what I witnessed firsthand over my three-day tour, I’d have to Say Yes, to Michigan; indeed.
Read our facility managers guide to building systems and cybersecurity.
 This article was written by Greg Orloff, the CBDO at IIoT World. Greg holds a Bachelor’s of Science degree in Environmental Science and Engineering from The Ohio State University, a Masters of Business Administration in International Business from Case Western Reserve University’s Weatherhead School of Management, and is a graduate of Ivey Business School’s Executive Leadership Program at Western University.
This article was written by Greg Orloff, the CBDO at IIoT World. Greg holds a Bachelor’s of Science degree in Environmental Science and Engineering from The Ohio State University, a Masters of Business Administration in International Business from Case Western Reserve University’s Weatherhead School of Management, and is a graduate of Ivey Business School’s Executive Leadership Program at Western University.



