Facility Managers Guide to Building Systems and Cybersecurity
How to Assure Vendors Establish and Use a Cybersecurity Hygiene
Don’t look now, but mainstream business leaders are learning that building systems may be the single biggest block of cybersecurity vulnerability in corporate America. Facility Managers, if you are one, can no longer be unaware, nor should they use traditional approaches to protect their turf when cybersecurity is concerned. Let’s take a minute and put some meat on the bones of these statements.
Facility management security execution
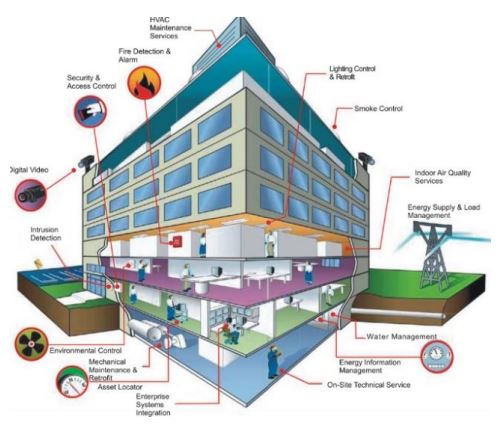
Today’s workplaces are typically equipped with numerous devices that are connected to the Internet. Each of those devices presents an attractive attack surface that serves hackers as a back door leading to interior domains.
Business leaders, such as Moody’s the investment rating organization, now focus on building systems because IoT (Internet of Things) devices are viewed as strategically valuable to the future of most every business and to life safety. Building systems include comfort and security (e.g. video surveillance, VoIP telephone and office machines). They also include sensors that drive heating, air ducts, water temperature, that can impact the very safety of a building’s occupants. Building systems have been around well before cybersecurity became an active concern. Building systems create the greatest number, by far, of unmonitored and unsecured back doors to most any business’ computer network. Moreover, these backdoors can lead to fatal consequences, if your building houses such businesses as hospitals, utilities, medical devices, pharmaceuticals, or the processing of water or wastewater. Cybersecurity threats highlight the work of Facilities Managers all of the way to boards of directors, who must consider enterprise risk, life safety and property value.
Research on Building Systems and Vulnerabilities
Cyber and Data. Both the Harvard Business Review (HBR) and Microsoft shined a light on building systems in the first half of 2019. HBR reported research stating that 60% of all cybersecurity breaches reported, in 2017, by publicly traded companies “…were launched through the computer systems of suppliers or contractors, up from less than 25% in 2010.” (1) A short time later, Microsoft reported research in its IoT Signals publication, issued the week before the Black Hat conference in Las Vegas, that 1,400 companies have been breached by nation states, using three building control devices as the top three points of entry: VoIP telephones; Video recorders; and Office machines. (2) Other building systems used in successful cyber attacks include HVAC, elevators with destination Building control contractors evolve from construction contractors to system integrators as software becomes the interface for managing the systems they deliver. Today’s workplaces are typically equipped with numerous devices that are connected to the Internet. Each of those devices presents an attractive attack surface that serves hackers as a back door leading to interior domains. dispatch, A/V collaboration devices, lighting, and business machines. The cyber attacks represented here focus their exploits on the data.
Facility Management Security Technologies

Building control contractors evolve from construction contractors to system integrators as software becomes the interface for managing the systems they deliver.
Other researchers and especially Joe Weiss at Control Global, focus on attacks that morph from essentially cyber to essentially physical, with the potential for destruction, injuries and death. They caution that many sensors used in smart buildings often have zero protection against cyber attacks. Such attacks can take over control of the sensors and the signals they generate, subverting them to cause both dangerous behavior of the target system (e.g. turbine, water and air) while at the same time sending misleading signals to monitoring stations. This happened when the famous Stuxnet malware disrupted Iranian centrifuges over the course of an entire year, while at the same time, destroying thousands of those centrifuges, a few at a time and doing so outside the view of highly advance monitoring systems used at this nuclear power facility. A second example is the Triton malware, frequently described as “the world’s most murderous malware”, was discovered after many months of disruption to an emergency shutdown system at a Saudi Arabian petrochemical plant.
Industrial equipment in high-rise buildings have many sensors with no IP address, limited or insufficient ability to be monitored. These sensors generate signals that are converted from analog to digital and then to packets with little means of assuring the integrity of the signal across conversions.
In general building systems should be considered to be generally “unsecured”, as this research proves and as evidence given the volume of attacks that gain initial entry through building systems. Thus, it should be clear to every Facility Manager that he or she needs to contribute to the cybersecurity solution or his or her facility or else be viewed as part of the problem.
How Facility Managers Secure Building Controls
Fortunately, there is an important, managerial (and non-technical) role for Facility Managers to actively participate in the solution without having to become a cybersecurity expert, or even conversant about cybersecurity. For those Managers willing to stand and deliver the solution to their department and be an important part of their Company’s response to cybersecurity concerns, there is the NeverCry Cyber Defense for Building Controls. The name “NeverCry” is a play on the enormous cyber attack that reached 150 countries in 2017 called the WannaCry. This attack started with building systems as its entry point.
The NeverCry Cyber Defense incorporates Facility Managers as integral leaders in the hardening of building control systems against cyber attacks. There are four important consideration for Facility Managers when thinking about cybersecurity and building systems. Facility Managers should:
- Retain the relationship between vendors and the organization, with no loss of leadership
- Serve as a senior manager concerned about the security practices used by their vendors when installing or servicing the organization’s systems.
- Cause each vendor to be responsible for developing its own cybersecurity hygiene. This is a written statement that identifies specific security systems the vendor will use when installing and servicing the organization’s systems. Specialty vendors, essential to the organization, may warrant financial assistance, though the typical cost is minimal Industrial equipment in high-rise buildings have many sensors with no IP address, limited or insufficient ability to be monitored. These sensors generate signals that are converted from analog to digital and then to packets with little means of assuring the integrity of the signal across conversions.
- Use incorporate the cybersecurity hygiene into agreements and statements of work and use limitations on liability for the vendor as a bargaining chip.
By addressing these considerations, the Facility Manager can do more to harden and secure the corporation than any other department, except the IT organization, and this is accomplished with nominal, if any, cost to the Company. There is no better way for the Facility Manager to become an important part of the cybersecurity solution.
Many Facility Managers willingly acknowledge the vulnerability of building systems to cyber attacks is disproportionately large and have quietly sought a solution. Others have held out and avoided confronting the issue. However, it will difficult for Facility to delay serious effort to closing the back doors existing in their building control systems. The consequences of such delay are both costly and dangerous, putting assets, life safety, privacy, reputation, and potentially national security at risk as well as one’s professional reputation.
Call to Action for Facility Managers
In keeping with the NeverCry Cyber Defense, Facility Managers are called on to achieve several important and reasonable objectives:
- Maintain Relationship and Leadership. Managers can retain full leadership by communicating to IT and vendors that cybersecurity will be addressed with very focused attention given to existing installations and active contracts. The focus is practical and forward looking with the goal of establishing each vendor’s capability and standard of performance regarding installing and maintaining sufficiently secure, or hardened, systems.
- Notify Vendors of Cybersecurity Concerns and Preparedness. Managers can further their active leadership by notifying vendors of increased concern about the vulnerability of building control systems and providing guidelines that shape how vendors might respond. The value of this notice to the Company is that it immediately protects the Company from being found negligent in the event of the type of breaches identified by the Harvard Business Review and Microsoft. The value of this notice to the Manager is that it establishes the Manager’s leadership regarding cybersecurity as well enabling adjustment to the Company’s portfolio of vendors, if necessary. For example, a vendor that resists committing to a mutually agreeable set of security systems will likely lose out on future contract opportunities and may even lose its status as an approved vendor. Or, a specialty vendor that is essential to the Company may warrant financial assistance, as circumstance might suggest.
- Prepare Vendor to Hardened Solutions. Substantially all Managers can expect to rely on vendors working with a third party to assist and guide its vendors in preparing their personnel to adopt secure procedures, since few vendors will have sufficient cybersecurity expertise to develop their own cybersecurity hygiene or prepare their own field personnel, The Cybersecurity Hygiene is core to the NeverCry Cyber Defense. A vendor’s cybersecurity hygiene is comprised of 40 to 60 security systems. These are selected based on the systems and devices that each vendor sells (e.g. HVAC versus video surveillance) and the markets they serve (e.g. general office versus finance, or industrial). This means that although there is considerable overlap in the security systems they use, the hygiene for one vendor is significantly different from other vendors. Each of these selected security systems is generally inexpensive, easy to implement and easy to understand (e.g. change default passwords, use two-factor authentication for administrative accounts, synchronize time and date between the application and the network clock, etc.). There is a point in the development of the Hygiene where the Facility Manager will arrange a meeting with the Company’s cybersecurity representative (which may the CISO or one of the CISO’s technical staff) and the vendor (which usually includes the third party assisting and guiding the vendor). The purpose of the meeting is to identify and clarify each of the security systems and to produce a mutually agreed upon “release candidate”, if not a “workable version,” of the Cybersecurity Hygiene. The meeting is seldom controversial, almost always productive, and reflects favorably on the Facility Manager. At least annually, a workable version will be updated by the two parties, at the initiation of the vendor who notifies the Facility Manager. Each vendor’s field technicians must be prepared to deploy the security systems that lead to hardening the devices and to encourage those personnel to identify specific security vulnerabilities found when performing work on the Company’s systems. Changing a vendor’s security awareness and behavior is best done in small increments over a period of several months. Many vendors elect to have a part-time (a.k.a. fractional) CISO provide guidance and support to their own personnel.
- Submit a Recommended Term Sheet. The Facility Manager and each vendor will be provided with a list of recommended terms and conditions that might govern a vendor’s performance regarding the Cybersecurity Hygiene. This is referred to as the “Cybersecurity Term Sheet for IoT Devices”. This term sheet will likely result in a contract addendum following review and discussion between the Company and the vendor and legal representation, as deemed necessary. The term sheet provides recommended language regarding: i) Obligations of the vendor to perform; ii) Right of the Company to review, accept or request modified performance; and, iii) Limitations to vendor’s legal liability. It is likely that this process may result in minor differences between the terms and conditions in one vendor’s addendum and another’s.
- Deploy a Software-Defined Firewall. The objective identified above can be achieve with no impact on the Facilities Department’s budget and can be considered Layer 1 of the Cyber Defense for Building Systems. Layer 2 is a software-defined network that unifies all building systems and configured to both prevent and control access to building systems for all devices with an IP address. This leaves unprotected only those devices that are not IP-enable and these devices require a defense preventing physical access.
Security Facility Management Third-Party Cyber Resource
Fortium Partners is the originator of the NeverCry Cyber Defense for Building Controls but is not the only resource able to advise and guide Facility Managers. Any Facility Manager and their building control vendors can be served by a third party that have:
- Experience working with integrators in the IT supply chain, cybersecurity, IoT devices including building systems
- Experience with the NIST Internal Report 8228 for IoT devices • Understand the cybersecurity considerations of the Company’s market
- CIO’s and CISO’s available on staff to serve as part-time CISOs for vendors in the IT supply chain (including the building systems channel)
- Contract language for construction (not just IT) projects
- Letters of attestation to provide, as appropriate
- Experience working with Purchasing Managers
Most companies have hundreds and thousands of building systems and other IoT devices, all creating back doors to sensitive data and those doors are not secured. Performing the activities described above produces an enormous pay off with no impact to the Facility Departmental budget and it provides a pathway to success and recognition. In place of years of stalled progress, a Facility Manager can accept responsibility and accountability without assuming material risk and add value to his or her career just as cybersecurity is bearing down on building systems.
The NeverCry Cyber Defense for Building Controls embraces and is consistent with the NIST IR 8228 and 800-171
For more information on the details of the NeverCry Cyber Defense use this link.
Notes:
(1) – link – July 10, 2018
(2) – link -Jul 30, 2019
![]() This article was written by Joel Rakow. He helps system integrators and their customers secure, buy, sell and implement solutions, making the IT supply chain stronger and able to conduct business more easily. It all starts with each party embracing its own cybersecurity hygiene.
This article was written by Joel Rakow. He helps system integrators and their customers secure, buy, sell and implement solutions, making the IT supply chain stronger and able to conduct business more easily. It all starts with each party embracing its own cybersecurity hygiene.



