Industrial Espionage is a major threat to the Manufacturing Sector
Industrial espionage is nothing new. Theft of trade secrets and corporate intellectual property (IP) such as proprietary manufacturing processes, formulas, recipes, and product designs has been happening for decades. And you probably already know this if you work in industries such as manufacturing, pharmaceuticals, and chemicals.
What is industrial espionage?
 Industrial espionage is sometimes credited for kick-starting the Industrial Revolution. In the early 18th century, a British silk spinner named John Lombe made a great effort to get hired at an Italian manufacturing company. At night, working by candlelight, Lombe made illicit drawings of the proprietary equipment the Italians used to spin silk on a large scale. Lombe returned to England and built the first successful powered continuous production unit in the world, based on the purloined technology.
Industrial espionage is sometimes credited for kick-starting the Industrial Revolution. In the early 18th century, a British silk spinner named John Lombe made a great effort to get hired at an Italian manufacturing company. At night, working by candlelight, Lombe made illicit drawings of the proprietary equipment the Italians used to spin silk on a large scale. Lombe returned to England and built the first successful powered continuous production unit in the world, based on the purloined technology.
The problem with getting an insider to steal trade secrets is that it takes time and money. The FBI recently busted six people in Houston, charging them with stealing trade secrets from a marine engineering company and sending the secrets to a manufacturer in China. The scheme took several years to develop and millions of dollars to fund—yet they were still busted. (Read more here.)
These days there’s an approach that’s much easier and less costly for the perpetrator: industrial espionage / cyberespionage.
In 2012, General Keith Alexander, who was NSA Director and commander of U.S. Cyber Command at the time, assessed the financial value of industrial espionage / cyberespionage losses at about $338 billion a year, including intellectual property losses and downtime due to cyberattacks. He called it “the greatest transfer of wealth in history.”
Where is that wealth of IP going? In many cases, it’s going to countries like China, whose government has designated several industries as “strategic.” Businesses receive government “intelligence data” (i.e., stolen IP), which enables them to improve their competitive edge and reduce time spent on R&D.
For many companies, such as those in the pharmaceutical sector, IP is much more valuable than any physical asset. And according to KMPG, operational information obtained from production systems, such as production and inventory data, can also be valuable as it enables competitors or suppliers to perform market manipulation and weaken negotiating positions.
So how would you know if cyber spies have already breached your OT network and stolen sensitive data from historians and ladder logic in PLCs, from which they can infer design secrets and other corporate IP? How about third-party vendors who connect directly to your OT network via laptops or USB drives, bypassing traditional perimeter defenses like firewalls and IDS/IPS devices?
Verizon says cyber spies are succeeding in stealing trade secrets
Deloitte writes that compared with more familiar cybercrimes such as theft of PII, “IP cyber theft has largely remained in the shadows.” That’s because, unlike retail and financial services organizations that are mandated by law to report consumer data breaches, industrial organizations are not required to report IP theft and other ICS intrusions.
However, check out these three data points from the Verizon Data Breach Investigations Report (DBIR):
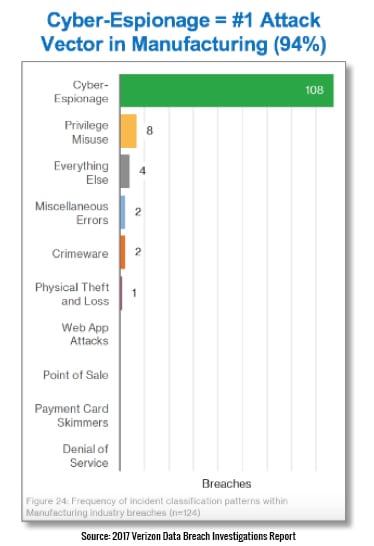
- Manufacturing is the #1 industry targeted by cyberespionage.
- Cyberespionage is by far the most predominant attack vector in the manufacturing sector.
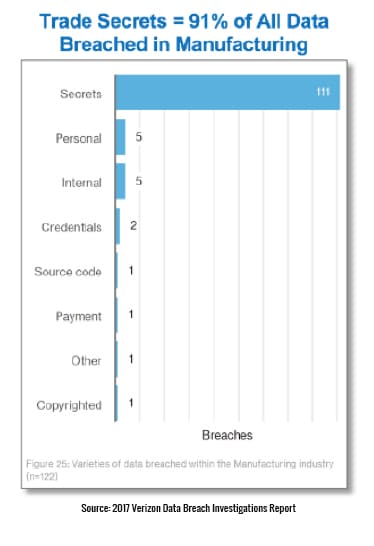
- Trade secrets are the #1 data type breached in manufacturing companies.
Verizon writes that the criminals’ goal is to “infiltrate the network, find out where secrets are kept, and then slowly siphon off the nectar for as long as they can.” Attacks typically begin with a phishing exploit allowing them to install malware that eventually enables IP theft.
The chart on the left reflects the prevalence of cyberespionage as the leading pattern of attack in confirmed breaches in the manufacturing sector.
What was stolen in those breaches? Secrets! More than 90% of the data stolen from manufacturers involves company intellectual property, as can be seen in chart on the right.
Why IT Solutions for Industrial Espionage Don’t Work for OT Networks
Traditional IT security technologies weren’t designed ICS environments. Active vulnerability scanning technologies like NESSUS cause downtime, while IT network monitoring solutions lack visibility into specialized industrial protocols.
And behavioral analytics developed for non-deterministic IT environments — using Bayesian models, for example — aren’t suited to the deterministic behavior of machine-to-machine (M2M) networks.
That’s why Gartner and other experts recommend using purpose-built OT security solutions.
Best Practice to avoid Industrial Espionage
Here are some best practices for manufacturers that want to keep their IP safe:
Get a complete asset inventory
Since you can’t protect what you don’t know about, get a complete and accurate inventory of all systems and critical assets within your environment. Many companies avoid this step because doing a manual asset inventory is complex and time-consuming. However, there are agentless, network-based technologies that can automate this process without being intrusive to sensitive operational systems.
Segment your OT network
A favorite tactic of cyberattackers is to compromise a host and move laterally from there. In the first Ukrainian grid attack, they compromised a PC on the IT network and leveraged an SSH connection to traverse through the IT/OT firewall to the OT network. Network segmentation or “zoning” — a best practice described in the ISA IEC 62443 standard (formerly known as ISA99) — makes it harder for bad guys to move between segments and compromise additional systems.
Conduct automated vulnerability assessments
It’s important to know how attackers are most likely to penetrate your OT environment, so you can address the highest-priority weaknesses based on risk, or at least compensate for them. Again, you can now leverage technologies that perform passive yet thorough vulnerability assessments— automated and continuously, rather than just once a year as with consultants and manual pen tests — that won’t affect production operations.
Patch vulnerabilities to the best extent possible
This is typical IT advice (e.g., WannaCry) — but it’s not always feasible to take a system offline to patch a Windows vulnerability or update device firmware (especially if it’s been running 24×7 for years), so at least deploy compensating controls to reduce risk.
Monitor OT network behavior for anomalies
One characteristic of industrial control systems is that they have a limited number of actions and states that are considered “normal.” If anomalous activity it detected — such as a host scanning the OT network or writing to numerous devices using multiple protocols (as Industroyer/CrashOverride does), it’s a potential sign of an intrusion that should be promptly investigated.
Eliminate unnecessary connections to/from IT networks and the Internet
If an external connection is necessary, say to allow a third party to perform maintenance, then monitor it closely for unusual activity such as spikes in bandwidth consumption or connections to suspicious domains.
Incorporate expert ICS threat intelligence into your system monitoring
Experts from CyberX and other companies continuously look for ICS threats and campaigns in the wild. The sooner you learn of such threats, the sooner you can put defensive measures in place.
Conclusions:
Cyberespionage is a massive threat to critical industries such as manufacturing, pharmaceuticals, and chemicals. A company that has its trade secrets stolen could find itself unable to compete against a competitor that delivers a cheaper product to the world market. Modern ICS/SCADA security solutions that continuously monitor your OT network for vulnerabilities and anomalous behavior are essential to reducing this risk.
This article was written by Phil Neray, VP of Industrial Cybersecurity at CyberX. Recognized as a Gartner Cool Vendor, CyberX provides a continuous threat monitoring and threat intelligence platform for IIoT and ICS/SCADA networks.