How to invest your first dollar in Industrial Cybersecurity?
Wanacry and NotPetya achieved what the experts were struggling to do: propel cybersecurity issues on board and raise awareness. Recent cyber-attacks have already cost businesses a lot and encourage top management to invest now their first money in their ICS cybersecurity. Once companies are ready to invest, the following questions arise: what level of security does my company need? What are the priorities? How to estimate the vulnerabilities of the industrial information system? How to get a return on cybersecurity investment?
How to invest in industrial cybersecurity?
Maintain a sufficient security level!
Every company seeks to sustain and maintain its industrial systems’ performance. This is called MOC (Maintenance in Operational Condition). It is about guarantying on the medium or long term the availability and the lifetime of its equipment. A strategy of sustainability is essential because renewing all or part of an installation, with a high initial cost, is expensive. Manufacturers also want to maximize the ROI and maintain the homogeneity of their facilities. This raises the question of how to conserve the networks security over time. This is what we call MSC (Maintenance in Safety Condition).
Recent examples of cyberattacks prove that old systems and configurations are the most vulnerable and the most targeted. The MSC’s objective is then to collect, aggregate and synthesize information dealing with threat and vulnerabilities’ changes. A good MSC strategy will maintain a constant level of security, adapted to the evolution of the threat, as well as monitoring and considering security patches.
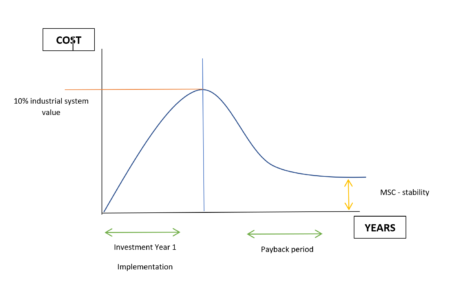
The MSC is, therefore, a crucial strategy for critical projects. Moreover, it is complementary to the MOC. With time, all manufacturers will have to integrate the MSC to the MOC to protect their networks from cyberattacks. If today the MOC is around 7 to 15% of the industrial IS value, merging MOC and MSC is a crucial step which does not cost more to companies (between 10 to 12%).
However, the MSC requires expertise in assisting the deployment of security patches, in enforcing security measures, and in handling security incidents. To do so, an initial investment in industrial cybersecurity is necessary to detect the vulnerabilities of its industrial system and to implement the organizational and material measures. We have two methods to master the cyber threat and understand the costs of effective and controlled security.
An “in-depth” cyber approach
A global cyber approach’s first step is writing down an ISSP (information systems security policy) that defines the objectives to be achieved, the staff implicated, and the resources allocated to the cybersecurity budget. It involves writing rules and procedures for your plant (access rights, incident response plan, restoration procedures, etc.). In France, since 2013, only critical infrastructures (OIV-private companies, national security structures) are constrained by the Military Programming Act to establish these rules, but this policy should gradually extend to the entire industry. Beforehand, the top managers need to be committed and the staff aware about the eventual cyberattacks. Indeed, the initiative of an industrial cybersecurity project cannot be planned without a real awareness from the directors. It is also recalled that a global cybersecurity strategy is the result of a collective work.
Once the budget is defined, we start identifying the existing. A map of the industrial information system (networks and equipment, flow matrix, programs’ inventories, system administration) allows us to determine a perimeter, facilitate the security incidents’ handling and report attacks. It is recommended to review the mapping each year.
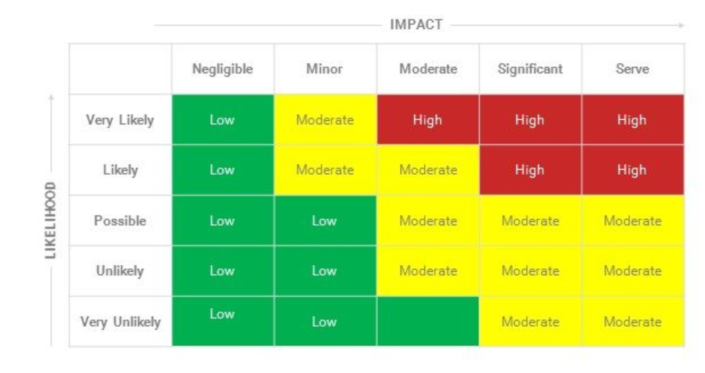
Then comes the risk analysis. Several methods are already used like EBIOS or MEHARI. It involves identifying critical processes, vulnerabilities, threats or the relevance and updating of components. It is necessary to know if these systems are sensitive regarding security of goods, people or industrial property. From the risk analysis, you can define a security target to know what you want to protect your company and allocate the necessary resources. When the risks are tolerated, we speak of residual risks (low impact/probability that the risk is dangerous for the industrial system – see diagram below).
To meet the basic criteria of security, it is necessary to implement appropriate security measures. After identifying what you want to protect, we define how to protect them. We are talking here about organizational and technical measures.
Organizational measures include knowledge of its industrial information system, training and awareness of staff (charter of good practice for example), cybersecurity by design, correlation of physical security premises and access control reaction in case of an incident relating to the authorities.
When it comes to technical measures, it’s more about: defining the roles and rights of IT administrators and users, authenticating them, partitioning the system (and thus avoiding the spread of a virus), securing protocols and equipment, logging events (to make detection easier and thus a quick intervention) or to install equipment that ensures the security of the industrial system, such as firewalls, demilitarized zones or intrusion detection tools (learn more about CyPRES, our detection probe).
By undertaking a global approach, combined with in-depth layers defense, manufacturers who wish to meet the challenge of industry 4.0 and protect their networks threats and security vulnerabilities, increase the resolution of incidents, reduce downtime and avoid financial losses.
The implementation of such a strategy and the deployment of solutions adapted to the critical industrial system take a year and require a financial commitment of up to 10% of the value of the industrial system (see diagram below).
A “pragmatic” cyber approach
Another strategy, implemented quickly (over a period of 2 to 4 months) and less expensive is also possible for a first cyber study. This approach allows the first level of security, with an optimized budget, for a better acceptance by the top management. This so-called pragmatic approach has the merit of securing the major vulnerabilities of the information system that can jeopardize the proper functioning of the process.
Here are the four steps to follow:
1. Inventory
The first step is the industrial system diagnosis. Any security project must include an assets’ inventory and their degree of openness to the outside to estimate the level of exposure. Beyond the knowledge of the industrial systems’ components, the inventory will assess the impact of an attack, facilitate the handling of security incidents and determine the protective measures.
2. Risk analysis
After making an inventory of the existing industrial systems, a risk analysis is carried out. In this process of identifying the essential vulnerabilities of the IS, we have developed a method, APERO (Analysis for the Evaluation of Operational Risks) which combines cybersecurity and operational safety. APERO enables the quick identification of the technical and organizational measures to set up to protect your SCADA.
It is based on fundamental criteria of availability, integrity, confidentiality, traceability, sometimes even accountability. In this analysis, we differentiate critical assets (information and processes) from supporting assets (components and subsystems).
3. Deployment of a technical solution
Few cybersecurity products on the market are designed for the context of industries. Today, it is essential to isolate your SCADA network from the IT network as well as third-party networks. To do so, manufacturers must implement a firewall that filters exchanges between networks and secures remote connections.
4. Training a cyber team
Investment in infrastructure’s security is not enough. To be optimized, the process of securing the industrial system must be coupled with training (theoretical and practical) in cybersecurity, adapted to the industrial environment. The goal is twofold. Sustain the investments and the measures implemented and be lsure that the IT and OT teams speak the same language. IT, OT and cyber experts need to collaborate.
This article was written by Elodie Perombelon, Communication officer at Cybelius and Vincent Nicaise, Marketing Manager and cybersecurity specialist at the same company. First the article was published here.