An overview of the IoT Security Market Report 2017-2022
This year was one of the most intense in terms of cybersecurity attacks affecting industrial control systems. For the first time since Stuxnet, a malicious toolset called CrashOverride/Industroyer targeted physical systems. The WannaCry and Petya attacks appear to have changed forever the attitude of industrial enterprises to the problem of protecting essential production systems. IoT security has become a major focus area for businesses. This focus is driven by the new attacks and threats, but also by the increasing number of IoT devices being connected to the internet.
IoT Analytics, a leading provider of market insights and strategic business intelligence for Industry 4.0 and the Internet of Things (IoT), published a 294-page IoT security report focusing on sizing the opportunity of the IoT security market for the period 2017 to 2022.
The report provide insights from the analysis done by the IoT Analytics analyst team who researched over 150 companies that offer IoT security technology solutions, reviewed 40+ implemented IoT security projects, undertook 25+ targeted industry interviews and attended several related conferences as part of the process.
What does the IoT security report contain?
- The IoT security report contains a detailed breakdown of the market by solution type(software, hardware, services), by segment(12 industries), by solution provider (top 10 vendors), by technology (21 technology areas), and by region (7 regions).
- The IoT security report also includes detailed company profiles of 10 large companies and 5 innovative smaller firmsoutlining their IoT security solutions, as well as an analysis of strategic partnershipsand M&A activities.
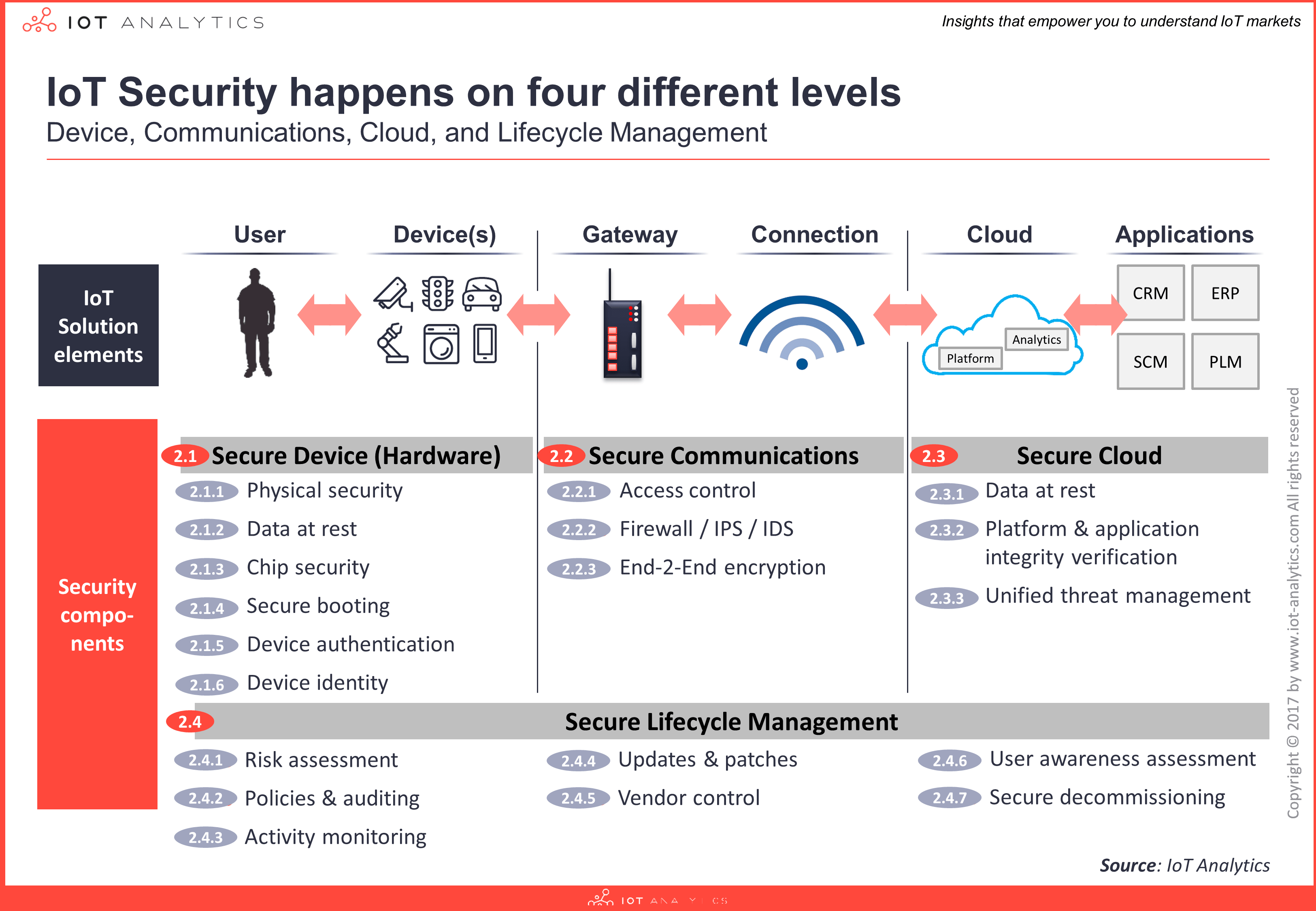
- An extensive IoT security segmentationis provided across 4 layers(device, communication, cloud, and lifecycle management) and 21 technology areas.
- Five key implementation considerationsare outlined for building secure IoT solutions, together with common best practices, an IoT security checklist and 8 detailed IoT security use cases presented in depth.
- A a comprehensive history of cyber security viruses(IT), cyber physical attacks(OT), IoT attacks and an evolution of cyber security solutions. Furthermore, today’s common threats in IoT are identified together with 5 types of IoT attackers and their motivation.
- The report also includes a detailed excel database of 150 independent IoT Security vendorswith extensive classification based on the vendor’s capabilities, estimated revenue, and industry focus across 60 sets of information.
A few insights
IoT security spending is currently estimated at $703M for 2017 and the fast growing market (CAGR of 44%) is forecast to become almost a $4.4B opportunity by 2022. Find out more about Three Types of IoT Security
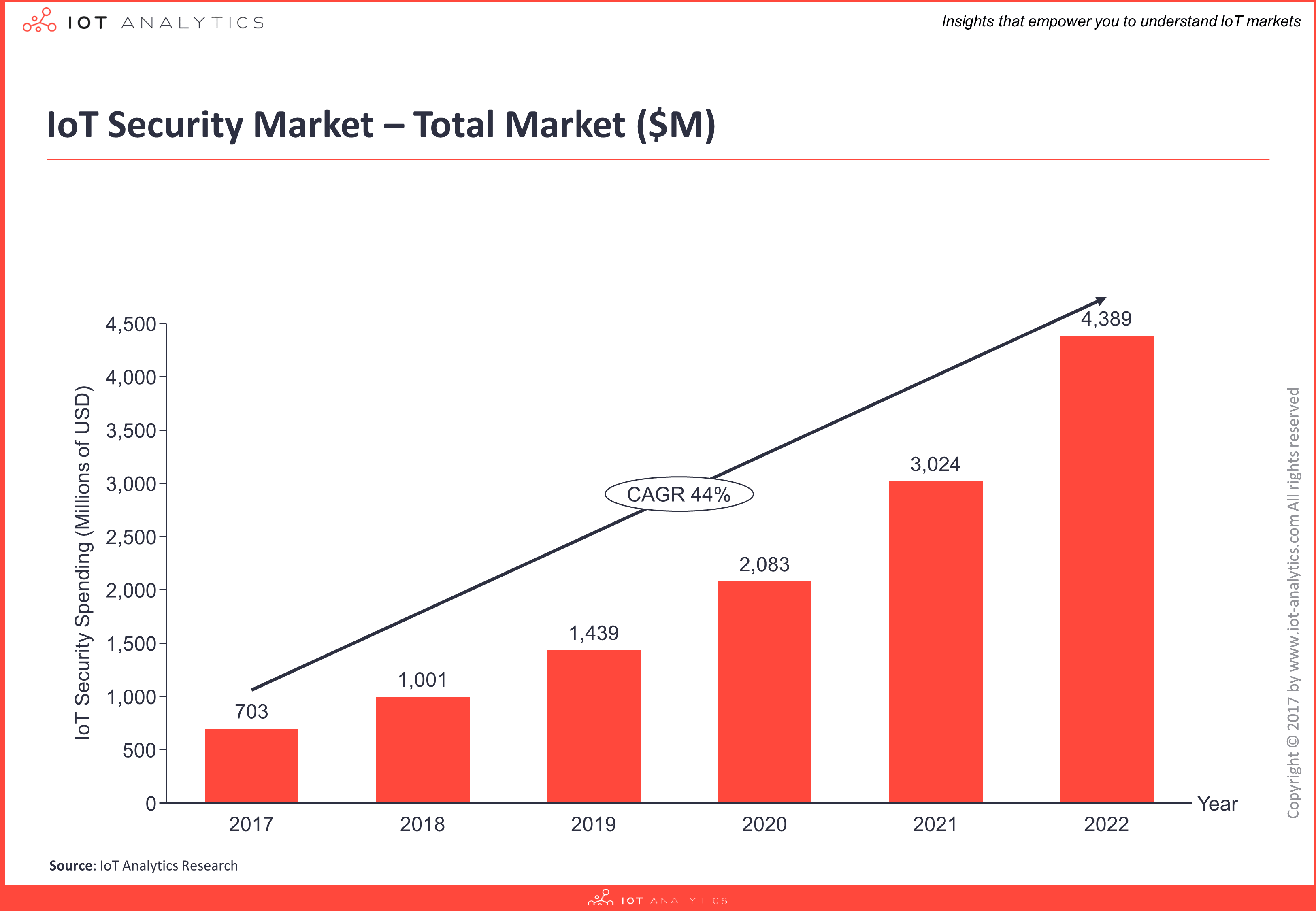
The IoT security market is an aggregation of innovative startups and established firms such as global chip manufacturers, infrastructure providers, as well as cloud and enterprise software companies. The top 10 providers account for over 40% of the IoT security market.
An extensive segmentation breaks down IoT security into 4 layers (device, communication, cloud, and lifecycle management) and 21 technology areas (including Services and Other) as in the exhibit below.
According to the report, at this point (Q4/2017) there is no single IoT security vendor that can provide the complete end-to-end out-of-the-box security solution. However, some companies offer more than others and together with their partner ecosystem some can provide a complete end-to-end IoT security solution.
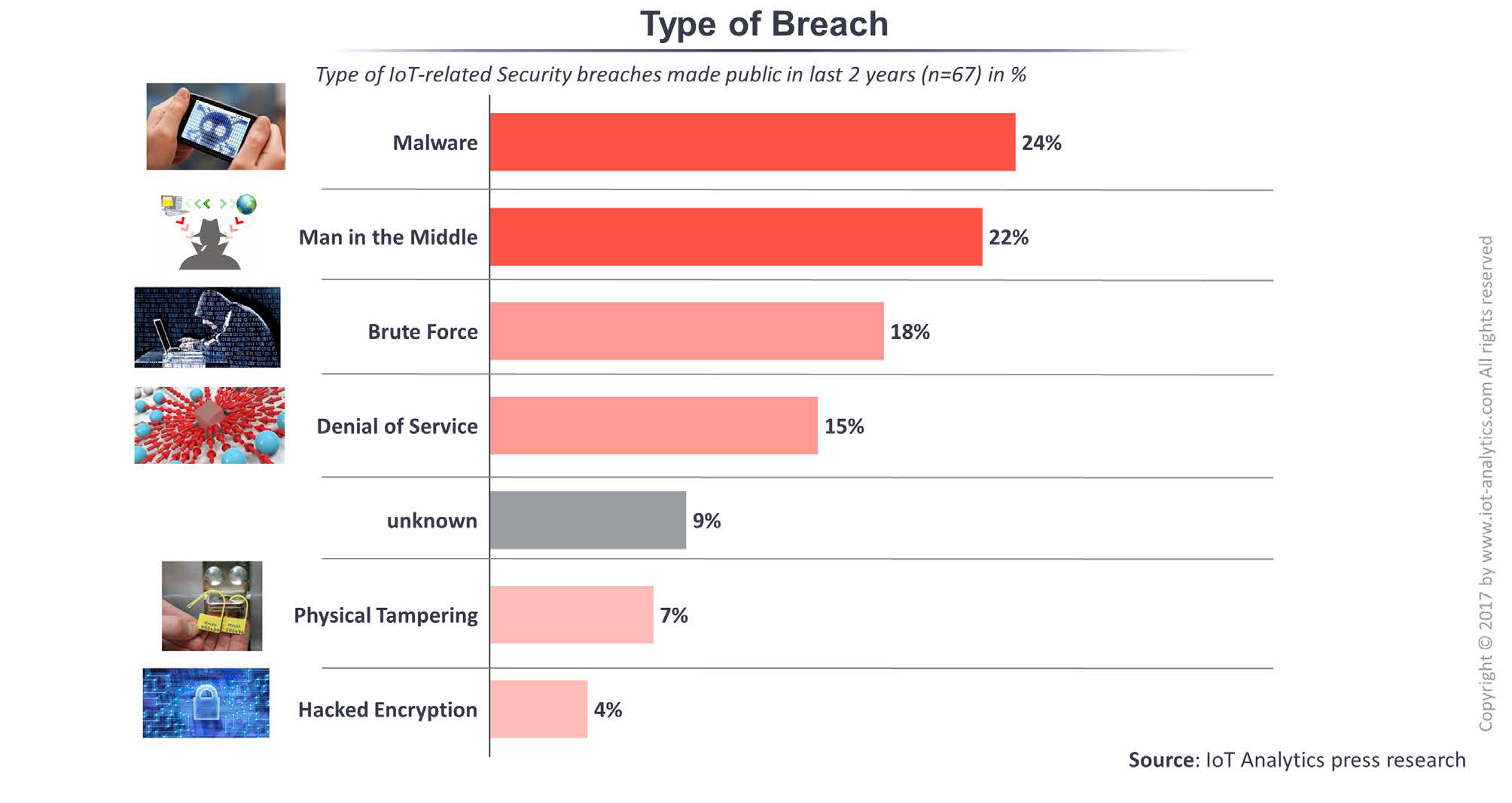
The analysis also shows what are the most common IoT breaches that happened in the last two years. Between 2015-2017 most of the breaches were caused by malware (24%), followed by human’s factor “man in the middle” (22%), brute force (18%) and denial of service (15%).
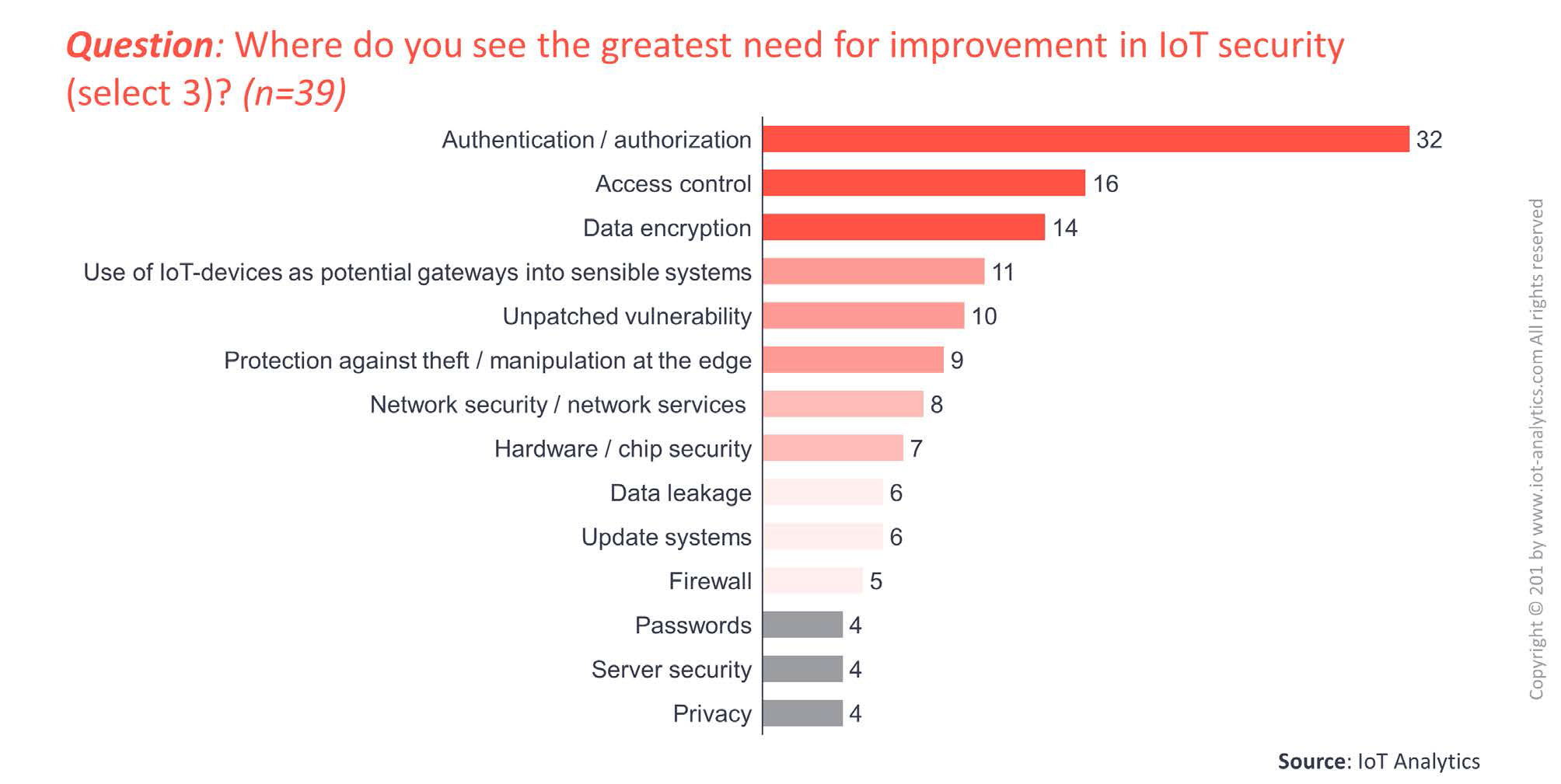
Being asked about the greatest need for improvement in IoT security, respondents are thinking that authentication/authorization is one of the biggest issues that needs to be addressed, followed by access control and data encryption. Firewall, passwords, server security and privacy were not considered as weakness by IoT security respondents.
The report also describes the top 6 trends and main challenges affecting IoT security. One of the dominant trends is increased automation of IoT security tasks (automated incident response, automated anti-virus or automated certificate management). And here is one example described by Padraig Scully: next-generation activity monitoring enables advanced anomaly detection, building on sophisticated machine learning algorithms. One case includes objectively classifying ‘good’ files from ‘bad’ files based on mathematical risk factors, which means it becomes possible to teach a machine to make the appropriate decisions on these files in real time. This method drives autonomous decision making and changes the way an IoT device understands, categorizes, and controls execution of every file.
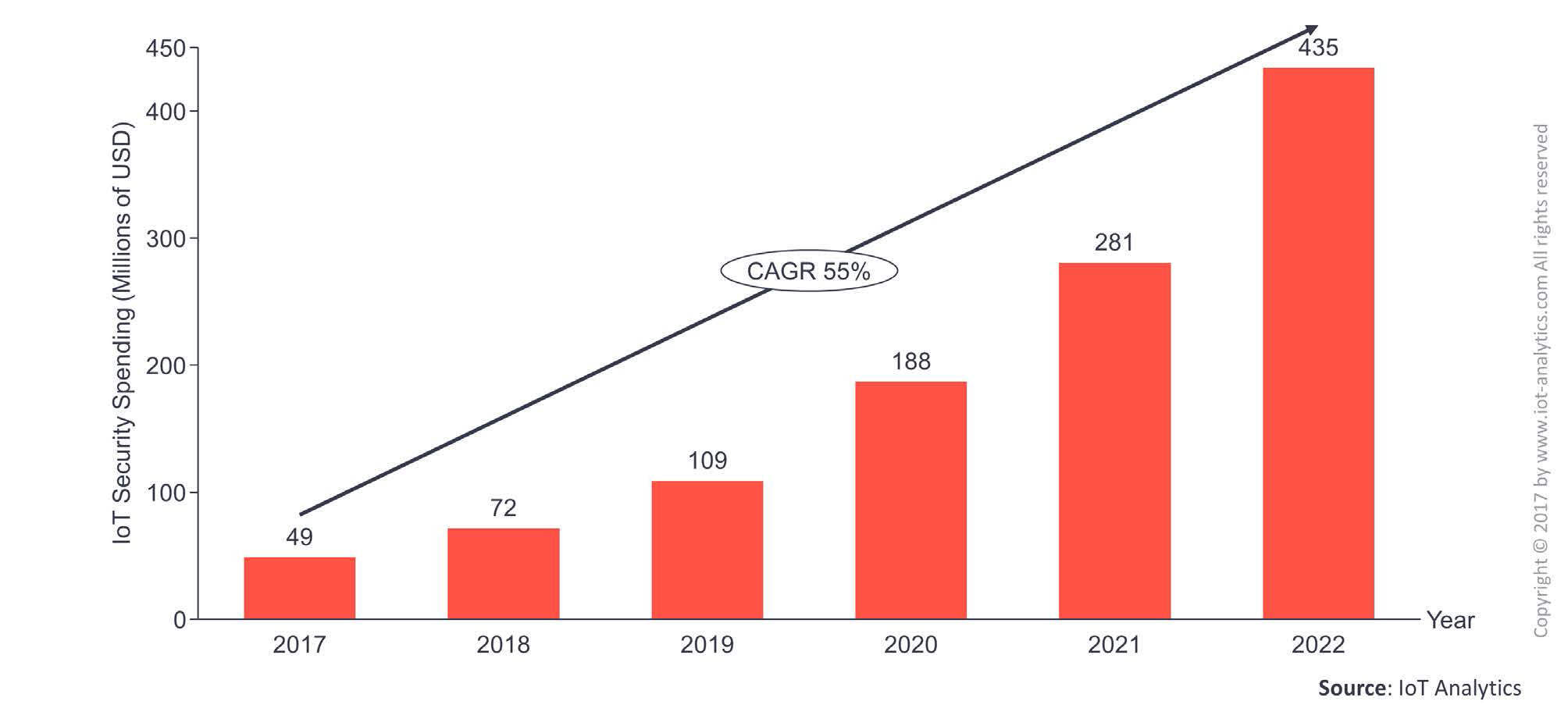
Another interesting aspect covered in the report is about the importance of IoT security in smart cities. Smart city is one of the fastest growing segment for IoT security. If in 2017 about 49 millions of USD are expected to be spend on IoT Security in smart cities, this number is about to grow 10 times, to 435 millions dollars in just 5 years.
For a detailed overview of the contents, see the Table of contents.
The IoT Security Report 2017-2022 is available for purchase here or download a FREE SAMPLE HERE. The IoT security market report is also available through a SUBSCRIPTION SERVICE giving members access to all content in IoT Analytics’ research stream.
Sorry, the comment form is closed at this time.




Pingback: An overview of the IoT Security Market Report 2017-2022 – indiz.de