The Transformation of the Tech Sector’s Second Most Famous Fruit Will Spark your Interest
I remember vividly the feel of that little side-wheel spinning rapidly in response to my overly exercised thumb’s pressure. Scrolling frantically through the myriad of emails and messages on my BlackBerry 7100 was a daily ritual. Then my thumb found a new workout routine when the trackball replaced the thumb wheel with the introduction of the 8100 and then the 8300, it required a little getting used to, but we made the transition. I have gone through multiple PDAs and smartphones over the years, but I must admit I was an avid fan of the BlackBerry. Then, like many, as the seasons changed I transitioned to a different species of fruit. So, when I was invited to attend an event at the NYSE sponsored by BlackBerry, both my thumb and I jumped at the chance to participate and find out the latest updates.

RIM’s BlackBerry was the bell weather of PDAs only half a decade ago with global subscribers peaking at ~85 million in 2013 but their market share fell off significantly in the years following. Although they are still in the device business, RIM’s direction pivoted when John Chen took over the helm that same year.
The arguable value proposition of RIM in the personal device arena was a secure, portable solution that offered global access to communication. Chen’s pivot leveraged the heart of the organization’s technical capability (the back end of the BlackBerry technology) in a different, but not completely new direction. RIM by name is Research in Motion, so the pivot leveraged this technical prowess, the BlackBerry Enterprise Server technology platform from personal devices into several other applications.
RIM’s resources were redirected into new emerging sectors, a main one being the automotive industry. The company’s QNX & Radar software technology is currently being leveraged not only as the foundation for vehicle infotainment systems but throughout the vehicle to optimize communications reliably, safety and securely. In fact, in terms of market penetration, they have shattered their previous 2013 record of ~85 million global users for their smartphones: Their technology is now incorporated into over 120 million vehicles, globally. Further, “The core technology has experienced over 20 years of in-field flawless deployment,” a bold and impressive claim. RIM’s BlackBerry® IoT Platform is also present in the Industrial, Medical, Security & Defense, Power Generation, and Rail market verticals.
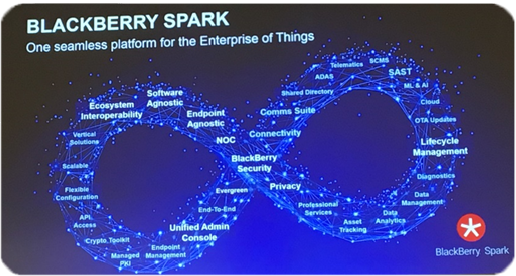
BlackBerry Spark, RIM’s latest offering, is positioned as an EOT (Enterprise of Things) platform for Ultra-secure Hyperconnectivity. During my conversation with John Chen, he explained that the strategy for Spark is simply, “To connect things safely and securely. Spark is a platform that is designed to enable two trends:
- The concept of hyperconnectivity – everything [devices, equipment, vehicles] wants to talk to everything else;
- Communication needs to be secure and private.”
The added nuance is that both trends need to be satisfied for “things” that exist in a dynamic environment, i.e. the things or devices move; globally.
Twenty years ago, the concept of keeping corporate data safe and accessible predominantly resided in ensuring the information never left the building or more specifically the servers that existed on site. Correspondingly, companies insured the necessary hardware, aka firewalls, were in place to mitigate an attack. Fast forward to a day when the workforce is now working from virtually everywhere around the world and corporate data may exist onsite, on the edge, in the FOG, or more often than not, in the cloud. Coffee shops, restaurants, and home networks are now the access point for a significant and growing part of the workforce. Vehicles could also be added to the list of virtual office environments. So, the complexity of managing the connection of things safely, securely, and privately is no small task.
Few organizations possess the breadth scope and technical aptitude to pull this off, but as the world continues to become more and more connected, decentralized, and digitized, a new perspective on how business is approached will need to be adopted. Authentication will become increasingly more challenging as additional location scenarios come into play. Geopolitical factors associated with, the IP address of a login point, network criteria, as well as atypical user patterns will all need to be analyzed to determine if an access situation is viable and if so what level access will be granted.
Michael I. Jordan, University of California, Berkley professor and researcher in machine learning, statistics, and artificial intelligence, pointed out that beyond the notion of keeping data safe and secure, creating environments where trust exists will be a necessity to catalyze individuals to interact and engage in online worlds where the value is exchanged. Beyond social networks and shopping sites interaction will move beyond traditional B2B and B2C models to C2C, D2D (device to device), and C2D (consumer to the device). However, this will only be possible if the new market creating platforms are layered on top of trusted infrastructure.
Time will tell if RIM’s Spark platform will meet these requirements and emerge as the dominant player but given their core competencies, they may just be one of the few organizations out there that have all the pieces of the puzzle to make it happen.
 This article was written by Greg Orloff, the CBDO of IIoT World. Greg holds a Bachelor’s of Science degree in Environmental Science and Engineering from The Ohio State University, a Masters of Business Administration in International Business from Case Western Reserve University’s Weatherhead School of Management, and is a graduate of Ivey Business School’s Executive Leadership Program at Western University.
This article was written by Greg Orloff, the CBDO of IIoT World. Greg holds a Bachelor’s of Science degree in Environmental Science and Engineering from The Ohio State University, a Masters of Business Administration in International Business from Case Western Reserve University’s Weatherhead School of Management, and is a graduate of Ivey Business School’s Executive Leadership Program at Western University.