The Cybersecurity Implications of Infrastructure Modernization
The adoption of new technologies in oil and gas facilities is a dual-edged sword. On one side, there are the obvious benefits of implementing industrial internet of things (IIoT) devices to improve efficiencies and reduce operational costs. On the other side, there are inherent risks associated with upgrading systems and with the cybersecurity infrastructure.
Cybersecurity Infrastructure: Case In Point
The Columbia Gas incident in metropolitan Boston last year, which produced a series of explosions in Andover, North Andover, and Lawrence, and resulted in more than 70 fires, one death, dozens of injuries, and the destruction or damage of more than 100 structures. Approximately 9,000 customers were left without power.
The New York Times reported that a system upgrade caused gauges that monitored pressure levels to be taken offline, and that unchecked over-pressurization triggered the blasts.
While human error was probably the cause of the Columbia Gas incidents, it could just as easily have been the work of terrorists.
Oil and gas executives are now acutely aware that once isolated OT networks charged with refining, mixing and the distribution of petroleum are increasingly connected to the “outside world” via the Industrial Internet of Things (IIoT).
In addition, modernization inevitably involves some degree of digital transformation, which exposes facilities to more cybersecurity infrastructure threats than ever before.
Attacks such as BlackEnergy, Industroyer, VPNFilter, and Wannacry are just a few of the recent malware campaigns that have affected critical infrastructures. The actors in some cases were rogue factions including nation states that hacked into industrial networks and caused havoc.
However, the threat from within is also omnipresent and highly significant, as insiders have ‘the keys to the kingdom’ — or at least know how to find them. Some studies show that insider threats account for more than 50 percent of all industrial and productivity cybersecurity incidents.
The IIoT Threat on IT Security Infrastructure
The Internet of Things (IoT) and the IIoT hold tremendous promise for improving oil and gas operations. Increasingly, companies are investing in the cost-saving and the productivity-enhancing benefits of networked smart devices that can communicate and coordinate with one another via the Internet.
The downside of IIoT is that few vendors and customers have fully considered the cybersecurity risks associated with the technology. The introduction of new access points into a company’s network, plus the current lack of security standards for IoT devices, can create holes for punching through perimeter defenses.
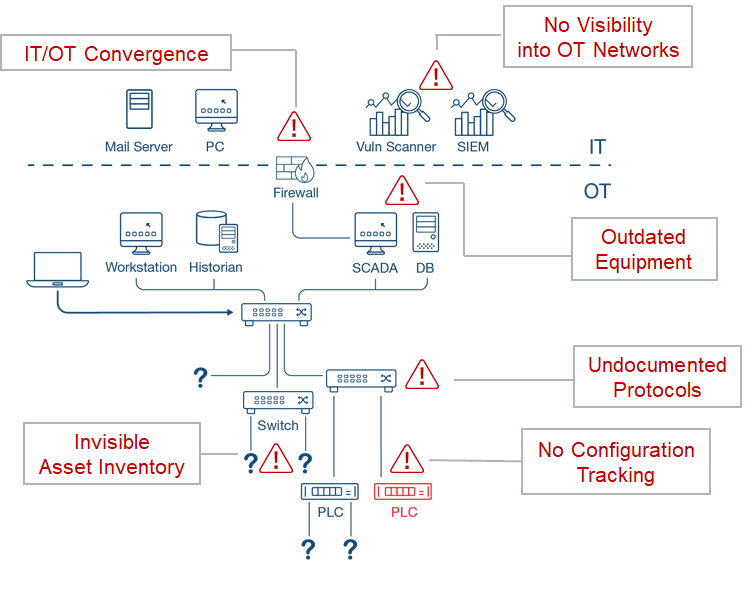
However, the planned or (worst-case scenario) unplanned introduction of IIoT devices into an enterprise network creates opportunities for a host of external and internal threat actors, including:
- Terrorists acting alone, independent of an organization or group, or is incited by an organization or group.
- State-sponsored adversaries acting on behalf of a government, whose activities can span computer-based as well as physical attacks.
- External cyber attacks caused by Hacktivists to promote a political agenda or a social cause.
- Internal attacks created by Malicious insiders such as a disgruntled employee or third-party contractor who is paid to exfiltrate information and/or cause damage to the organization.
- Or unintentional mistakes due to human error that causes damage and/or downtime because of incorrect changes to industrial processes or equipment.
Yet another variation, account compromise, resembles an insider attack since it occurs when an external attacker hijacks an authorized user’s account (employee, vendor, integrator, etc.). These are typically achieved using social engineering techniques such as phishing emails and a “call from the IT department” requesting the user’s ID and password.
Top Cybersecurity Infrastructure Risks
1. Default Passwords
Most IIoT devices are pre-configured with a default password, which is clearly a time-saver for IT staff. However, this benefit is also a major security flaw. When hundreds of thousands of devices share the same default password, attackers can easily compromise organizations that have neglected or intentionally decided not to change it.
2. Missing Patches
This is another huge problem area for organizations, because many IIoT devices cannot be patched or vendors do not issue patches for known vulnerabilities.
3. Too Many Devices to Manage
In many organizations, the list of IIoT devices is endless and extends beyond traditional operational technology (OT) to alarm systems, cameras, thermostats, vending machines, etc. Even the most apparently harmless device, can pose a threat. For example, an IoT coffee-maker should never be connected to an IT or OT network as the machine has no security features.
Regardless of the IIoT device type, all of them can be used by attackers as a stepping stone to compromise IT and OT networks. For example, many IIoT devices use ports that are exposed to the Internet, and which can be used to bypass the firewall. Once inside the network, a hacker can do extensive damage to IT and OT infrastructures and move laterally between them. Think data breaches, viruses, ransomware, sabotage, and data exfiltration.
One way to combat the cybersecurity risks and broader attack surface created by modernization initiatives, and mitigate the threat cyber incidents and human error pose to production and environmental control systems, is to converge IT and OT security groups. While challenging, such collaboration can mitigate the risks and vulnerabilities that span these two infrastructures, simultaneously facilitating the implementation of security best practices.
More about Securing Network Infrastructure
Here you can read more about Unifying IT and OT Security and Defense Measures.
![]() This is an excerpt from Michael Rothschild‘s article originally published here. Michael is Senior Director of Marketing at Indegy and has more than 20 years of experience in IT security. Michael has worked in product management and marketing roles with Thales, RSA, SafeNet (now Gemalto), Dell, Juniper Networks and Radware. In his spare time, he volunteers as an Emergency Medical Technician.
This is an excerpt from Michael Rothschild‘s article originally published here. Michael is Senior Director of Marketing at Indegy and has more than 20 years of experience in IT security. Michael has worked in product management and marketing roles with Thales, RSA, SafeNet (now Gemalto), Dell, Juniper Networks and Radware. In his spare time, he volunteers as an Emergency Medical Technician.



