How to better manage your digital attack surface risk
As organizations shift to the cloud in droves, their digital attack surface continues to rapidly expand. And with the number of threats rapidly increasing, security leaders need to enhance their attack surface risk management. We explore how a unified cybersecurity platform can help improve your defenses against cyber risk in comparison to point products.
Digital transformation has accelerated the shift to the cloud, enabling organizations to innovate more, faster and expand beyond traditional office environments. However, this has led to new complexity regarding effective attack surface risk management. We discuss how to better understand, communicate, and mitigate cyber risk across the three phases of the attack surface risk lifecycle as well as how to simplify security management.
What is attack surface management?
Attack surface management (ASM) is the continuous discovery, assessment, and mitigation of an organization’s IT ecosystem. This differs from asset discovery and monitoring in that ASM evaluates security gaps from the attacker’s perspective, including risk across people, processes, and technology.
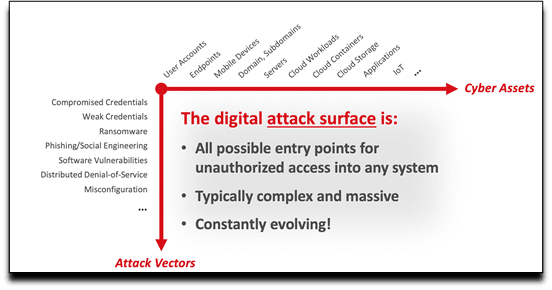
Why security leaders need better risk management
As we mentioned earlier, digital transformation has caused an enterprise’s attack surface to expand rapidly—50% of organizations are adopting a cloud-native approach to support both employees and customers, and the number of connected devices is expected to climb to 55.9 billion by 2025. The shift to the cloud and dramatic increase of connectivity gives malicious actors new (often unmanaged) attack vectors to target.
Evidently, security leaders need to enhance their risk management strategy and procedures, not only to avoid costly ransomware attacks and disruptions to workflows, but also to meet new mandates for much needed cyber insurance.

So, how can security leaders stay on top of their attack surface and ahead of the bad guys? By leveraging a unified cybersecurity platform that enables continuous security visibility and monitoring across the discovery, assessment, and mitigation phases of the attack surface risk lifecycle. Let’s dive deeper into how a platform can enhance attack surface digital transformation risk management versus utilizing point products.
Discover your digital attack surface
First, you need total visibility to be able to discover your attack surface. Siloed point products across endpoints, users, devices, cloud, networks, etc., limit overstretched security teamsfrom taking stock and they don’t have time for a manual audit
Also consider that new projects with open source dependencies and user/device accounts are spun up instantly, meaning you need to be able to see your entire ecosystem as it changes, not after.
A cybersecurity platform with broad third-party integration allows security teams to view their entire ecosystem from one dashboard, saving valuable time and empowering them to better assess cyber risk.
Assessing your cyber risk
Being able to see your entire ecosystem as it changes is the first step; next, security teams need to assess and prioritize any weaknesses or vulnerabilities. This doesn’t just apply this to systems, but user types as well—for example, executive level employees are the most common targets for business email compromise (BEC). Also, we’ve seen an uptick in campaigns targeting software supply chains and DevOps pipelines, meaning processes also need to be evaluated for any security gaps.
As always, this needs to be an ongoing process. For example, user behavior can change mid-session and require access termination. A unified platform with deep, native integration across the enterprise enables organizations to implement a Zero Trust strategy, supporting the need to continuously verify and assess any users, applications, and devices with access to your IT infrastructure.
Unlike point products that end up with siloed data, a platform can continuously collect and correlate deep threat data across your attack surface (endpoints, networks, cloud, and email) to produce fewer, but higher-confidence alerts. This allows security teams to narrow-in on and prioritize critical or high security threats and risks in smart factories without time-consuming, manual cross-product correlation. It also enables organizations to address the detection and response requirements that modern cyber risk insurance policies are demanding today.
Mitigate risk
Finally, while discovering and assessing risks across your digital attack surface is important, it’s also important to receive remediation recommendations and be able to automate mitigation wherever possible. A unified platform with security controls across multiple environments can help to automate the mitigation of high priority risks, like the application of virtual patching capabilities to limit the scope of an attack and allow security teams to focus on further investigation. With the skills shortage introducing very real challenges to managing the attack surface, the ability to consolidate tools and leverage a unified platform can also help with risk mitigation.
Next steps
Better digital attack surface management starts with the right tooling: a unified cybersecurity platform with broad third-party integrations that seamlessly fits into your existing security stack. Consider a platform backed by innovative security capabilities such as XDR, continuous threat monitoring, risk assessments, and automation to alleviate security teams, accelerate detection and response, and meet compliance and cyber insurance requirements.
Originally this article was published here.



