
Industrial IoT: Security Challenges and Expectations
Companies in manufacturing and transportation-related industries have significantly benefited from the integration of industrial IoT technologies (IIoT). Past insurmountable technical challenges have been eliminated with ease since IIoT platforms have come into widespread use especially in…

Cybersecurity Threats – The New Reality for Utilities
Cybersecurity experts agree: Cyberattacks are the new reality for utility companies. On Jan. 10th, 2018, a major power outage hits the Consumer Electronics Show (CES), Las Vegas. For nearly two hours, participants were reminded that without electricity,…

Digital Health’s cybersecurity imperative
If you haven’t already heard, the age of digital health is upon us. And for healthcare providers, patients and consumers, it’s about time.What is digital health?Digital health, sometimes referred to as eHealth or Mobile Health, refers…

How to implement baseline security measures for every ICS organization
The development of Industrial Control Systems (ICS) over the past two decades has changed the face of many industries. Operational Technology (OT) – largely industrial equipment – has become increasingly connected, and the integration of Information…
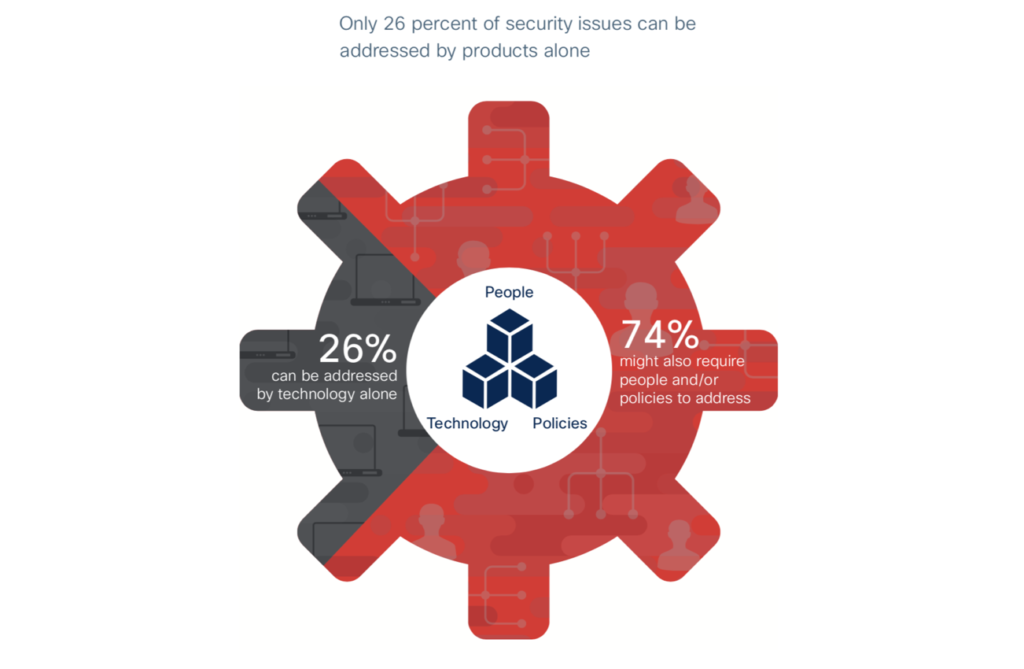
Cisco’s cybersecurity recommendations/solutions for manufacturing
Hannover Messe has been a great success for many companies this year. One of the topics we had on our radar at this event was cybersecurity. As Oliver Tuszic, VP and General Manager of Sales at…

The importance of the intent-based security in smart manufacturing
Industrie 4.0, offers great promise for manufacturers to optimize business operations. The key to any successful Industrial IoT project lies in the factory data. Industrial customers need seamless, secure access to this data to make better…

Innovation Review: Transport Layer Security during the IoT Forum
This week together with our Chief Innovation Officer, Greg Orloff, a new addition to our team, I was in Silicon Valley, at the IoT World Conference and also attended the IoT Forum, a community that meets…

Why food & beverage companies should crack down on Cyber threats to ICS
When we buy groceries at the supermarket, most of us check the ingredients and expiration dates of packaged goods. But how can we be sure that the products we bring home are safe to eat and…

RSA Conference in Review – “Securing What Matters”
Coming off of San Francisco’s RSA Conference, the best way to describe the event is “sensory overload.” An estimated 45,000 technology and cybersecurity professionals descended upon Moscone Center – but the crowds overflowed into local bars,…

The Importance of Security by Design for IoT Devices
We’re on the verge of an explosion of IoT-related products and services and the security for IoT devices is a concern. We all know that the Internet of Things or IoT has started to disrupt consumers,…


