
Search for: runsafe security

Protect Critical Infrastructure With Runsafe Security’s Alkemist
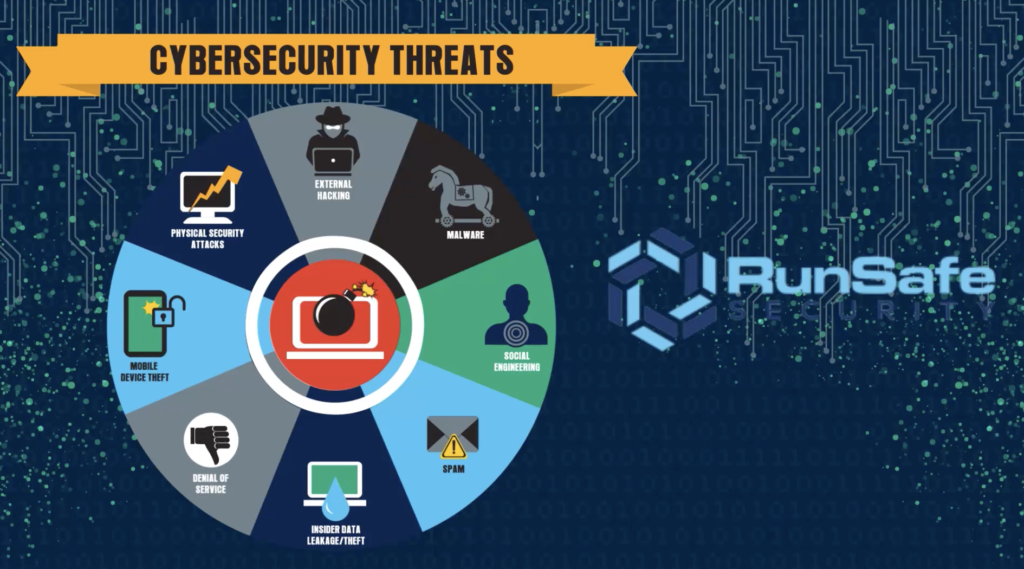
Hackers are having increasing success penetrating the operating technology and industrial control systems underpinning data centers, utilities, manufacturing plants. As organizations incorporate smart devices, connect to the Internet of Things, and utilize the cloud to optimize performance, new attack vectors – and cyber vulnerabilities – are created. Skilled cybercriminals only need to find a single […]
Read more →
Cybersecurity Trends to Prepare for in 2022
Recap of Cybersecurity and Cyber Attacks in 2021 Dare I say that the past year has been…drumroll…unprecedented…in the realm of cybersecurity and cyber attacks? Here are some statistics to showcase what the industry has endured over the past 12 months: With the trends over the previous year, ransomware costs are expected to reach $265 Billion […]
Read more →Addressing cybersecurity vulnerabilities in the changing LINUX landscape
Linux is a prevalent component of nearly every workload: more than 90% of cloud workloads and 70% of web servers run on it. Like all technology solutions, Linux has continued to evolve over time, potentially opening you up to new cyber security threats. Bad actors often have an advantage because they are working against known security measures […]
Read more →
Using Security Monitoring to Address Cybersecurity Threats
Joe Saunders, CEO of RunSafe Security, recently hosted a panel discussion on Monitoring Open Source Software in SAAS Infrastructure. His panel included business leaders in the software, technology, and security sectors: Jonathan B Fishbeck, Founder and CEO of EstateSpace, LLC, a Managed Security Services Provider (MSSP) that helps people reduce risk, retain property assets, and protect […]
Read more →
Cybersecurity Tactics to Prevent Jackware Attacks on Embedded Devices
Ransomware is a serious cybersecurity challenge that is growing at uncontrollable rates. Every 11 seconds, a new organization falls victim to a ransomware attack. And by the end of this year, the cost of ransomware to businesses is expected to surpass $20 billion. In this article we present some cybersecurity tactics to prevent jackware attacks […]
Read more →
Three Ways to Help Improve the Nation’s Cybersecurity
By now, you’ve heard about Executive Order 14028 on “Improving the Nation’s Cybersecurity” which President Biden signed in May, 2021. It begins by stating, “The United States faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy. The Federal Government must improve […]
Read more →
Industry Feedback from Executive Order on Improving the Nation’s Cybersecurity
The recent signing of the Executive Order on Improving the Nation’s Cybersecurity has spurred much discussion among the industry. IIoT World asked for input from leading cybersecurity experts and organizations regarding the EO, and we’re sharing the discussion with our community. Here are some excerpts from our exchanges on LinkedIn: “Having the EO emphasize […]
Read more →
Cybersecurity to Improve Profitability
Cybersecurity has financial benefits, offers product differentiation, and smooths out the patching processes both for product manufacturers and their customers. The importance of cyber defense will go up over time. Cyber defense and security for embedded systems is justified using a total cost of ownership approach, as quantifying economic benefits will help justify faster adoption. […]
Read more →Cybersecurity Gaps in Scanning and Patching Vulnerabilities in Software
Current strategies of scanning for and patching vulnerabilities in software leave a huge and highly-exploitable security gap. Recent research by RunSafe Security partners show that current strategies of scanning for and patching vulnerabilities in software leave a huge and highly-exploitable security gap. When measured against NIST CVEs (Common Vulnerability Enumerations from the National Vulnerability Database), […]
Read more →Cybersecurity for Embedded Systems
All critical infrastructure is under cyber attack, all the time. The attack on the Oldsmar, FL water supply is a good example. And it’s getting worse; vulnerability to cyber attack is increasing as the embedded devices controlling these critical infrastructures become more connected. The DevOps approach to software development offers an antidote—an opportunity to embed run-time […]
Read more →
Cybersecurity for Shared Cloud Environments
In its recent Cloud Workload Protection Platform (CWPP) research note, Gartner identified memory exploit protection as an essential component of any organization’s CWP strategy (Gartner, Cloud Workload Protection Platforms, 2020): “Exploit Prevention/Memory Protection–application control solutions are fallible and must be combined with exploit prevention and memory protection capabilities…”—Gartner CWPP 2020 Cybersecurity Considerations for the Cloud Cloud deployments […]
Read more →