Should You Start with Network or Endpoint in OT Security?
OT/ICS security teams hear different perspectives from different groups and are often left confused as to the best place to begin.
In Verve’s 30 years of experience in OT/ICS cyber security and reliability services, we often hear a debate about the best way to address cyber security risks. You hear about new vulnerabilities in ICS devices (40% more than last year). You hear about new threat actors targeting critical infrastructure. You hear about offerings from OT/ICS cyber security vendors.
And we’re asked questions such as:
- Isn’t it better to stop the attacker before they get through the perimeter into the OT network, rather than focus on protecting OT internal networks or endpoints?
- Isn’t it impossible to patch and harden OT endpoints, so network detection is really the only option?
- Once the attacker gets through the perimeter, how do you stop them?
- Isn’t the priority to identify malicious packets communicated to PLCs or controllers rather than try to monitor more IT-like devices in the OT systems?
Their real question they’re asking: Where should we begin in our ICS/OT cyber security program?
- Network Segmentation?
- Assessment?
- Asset Inventory (you can’t protect what you can’t see)?
- Vulnerability Management?
OT/ICS security teams hear different perspectives from different groups and are often left confused as to the best place to begin.
Where to start your OT cyber security program
The United States Cybersecurity & Infrastructure and Security Agency (CISA) recommends defense in depth as a way to protect OT/ICS environments. This includes items from policies & procedures to network, access, and endpoint protection. Through all of their advisories for new vulnerabilities and new threat actors, CISA is consistent in its advice. The good news is there are a set of programmatic things you can do to protect your organization.
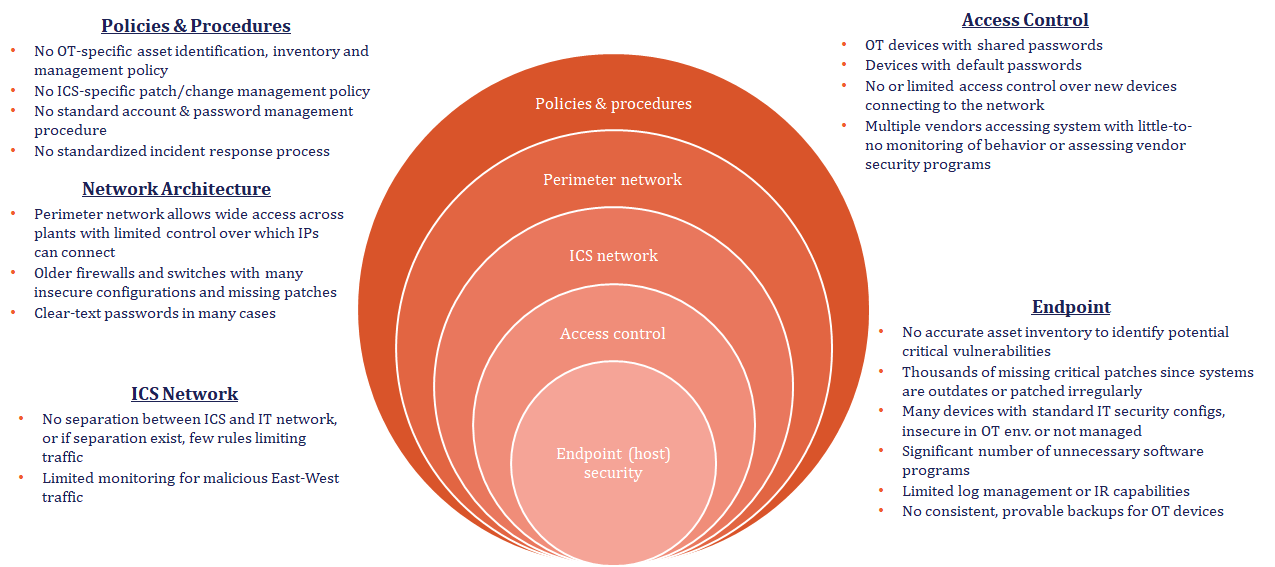
Improving the reliability and security of ICS networks, Verve has successfully deployed in thousands of environments and conducted hundreds of site assessments of cybersecurity on OT systems. These deployments have called attention to how differently every organization approached their cybersecurity program, but it’s become evident the most successful programs start the same way.
Conducting a robust vulnerability assessment of the ICS/OT attack surface is key to getting your program right. While there is a temptation is to jump in to “do something” to demonstrate progress, organizations tend to neglect the importance of first assessing the situation because of how long it can take. While these companies jump to take immediate actions they know they will eventually need (such as network segmentation or threat detection), this is not the most effective or efficient approach. And may end up costing you in the long run.
For these reasons, we recommend beginning with a Technology Enabled Vulnerability Assessment (TEVA). A TEVA gathers detailed visibility of the risks of the environment and prioritizes those risks. Unlike a traditional vulnerability assessment, it uses technology that gathers detailed asset inventory directly from the endpoints. This results in prioritizing the risks and remediations to gain the greatest maintainable security in the least time and cost.
Benefits of a technology-enabled assessment for endpoint-enabled security:
- TEVA provides an accurate asset inventory with data directly from endpoints in the network rather than relying on spreadsheets or scans for immediate response support or vulnerability assessment. A robust asset inventory is critical to the entire program and acts as the foundation to build upon.
- TEVA has several advantages over the traditional manual/survey-based assessment approach because it leverages technology, such as:
- Lower cost because of the automation of the data collection and no need for travel to each site
- Fact-based data on endpoint vulnerabilities rather than relying on surveys
- Accelerated time to remediation using the technology employed in the assessment
- Real-time updating of the assessment so that as remediation is conducted, the assessment updates risk scores
- The technology enables a detailed view of current network rules and protections by analyzing ACLs and configurations of firewalls and switches
- Although network segmentation will certainly be part of an ICS/OT security program, starting with that effort often leads to challenges due to the time it takes to deploy new hardware and the moves of systems required. In addition, many segmentation efforts stall because of a lack of visibility into the endpoints that you actually want to segment, which the assessment provides.
- Network anomaly detection is not usually a good place to start given the cost and time to deploy those solutions in most OT networks with the need for span ports, taps and other infrastructure necessary to provide the level of depth required.
- TEVA provides the foundation necessary for deployment of endpoint protection not only because it identifies all of the assets and their OS versions and software in the environment, but also because it provides the right access to deploy those tools once the technology is enabled.
The tech-enabled vulnerability assessment is defined by a 360-degree view of the most significant threats to the environment are, such as …is the biggest threat the communication at layer1 between two PLCs or between an HMI at level 2 and a PLC at level 1, is the biggest threat that an attacker will reach the IT system and ransomware will spread into OT because it’s connected to IT, is it that a targeted attacker will find a way through the perimeter and run malware or gain privileged access to HMIs and servers to conduct the rest of the campaign, is it that they will use that access to take advantage of a vulnerability in a PLC or controller to cause a DOS or other impact on that device?
It also determines what the organization’s starting point is, whether IT/OT separation exists, is it well configured, do you have significant software vulnerabilities, etc. Then consider what is most timely to execute: How long does a particular project take? What enablers are required to do the first thing?
This article was written by Adnan Alawneh, OT/ICS Cyber Security Strategist & General Manager, Verve Industrial and originally it was published here.



